LEVEL-3
8 / 3 / 2024
1. Speed Control of BLDC Motor:


Skills and knowledge acquired: Learned to use and control the speed of a brushless DC motor(BLDC) by using power supply to function it and also explored its various applications and advantages. BLDC has high efficiency, better controllability, and power-saving advantages compared to other types of motors. Also, learnt about the rotary potentiometer by making use of it in this task.
2. Interfacing RTC Module and displaying the data on serial monitor(IOT):
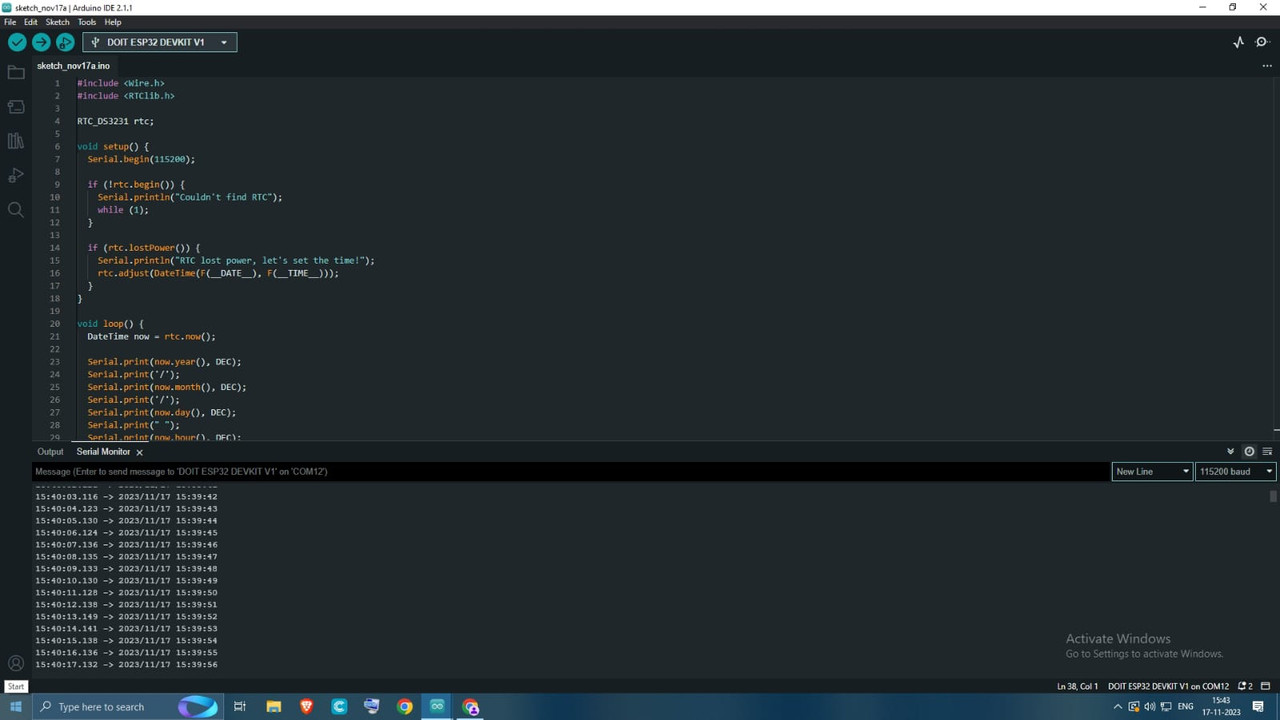
Skills and knowledge acquired: Learnt to interface a DS3231 RTC Module with ESP32 and display the real-time and date on the serial monitor.
The DS3231 is a low-cost and extremely accurate real-time clock (RTC) with an integrated temperature-compensated crystal oscillator (TCXO). The device incorporates a battery input and maintains accurate timekeeping when the main power to the device is interrupted. The RTC maintains seconds, minutes, hours, day, date, month, and year information very accurately.
3. Introduction to Cybersecurity (Cybersecurity & Cloud Computing):
Skills and knowledge acquired:
Cybersecurity: It is the technology designed and developed to protect computer networks, systems and devices from unauthorized and illegal access, damage, hacking and to protect businesses confidential information.
*Confidentiality: It is one of the main principles of Cybersecurity that asserts that information and functions can be accessed only by the authorized parties. Application: Military Secrets
*Integrity: It is one of the main principles of Cybersecurity that information and functions can be modified in any way only by the authorized parties. Application: Traffic Control Systems
*Availability: It is one of the main principles of Cybersecurity that information and functions must be available on demand according to agreed-upon parameters based on service levels.
*Malware: It refers to any software intentionally designed to cause damage to a computer, server, client, network, or to perform unauthorized actions on a computer system. Malware encompasses a variety of harmful or intrusive software types, including viruses, worms, Trojan horses, ransomware, spyware, adware, and other malicious programs.
*Phishing: It is a type of cyber attack that involves tricking people into giving out sensitive information, such as login credentials, credit card numbers, or other personal data, by impersonating as a trustworthy person/party. It can be carried out via email, text messages, social media, or other online communication platforms.
*Social Engineering: It refers to the manipulation of individuals to gain unauthorized access to sensitive information, systems, or networks. Unlike traditional hacking methods that focus on exploiting technical vulnerabilities, social engineering exploits human psychology and behavior.
*Cybersecurity Frameworks: They provide structured approaches for managing cybersecurity risks. These frameworks offer guidelines, best practices, and standards to help organizations protect their information technology systems and data. They are helpful for creating a reliable cybersecurity strategy, ensuring compliance with legal and regulatory requirements, and establishing a common language and set of standards for cybersecurity efforts.
*Cryptography: It is a method of protecting confidential information and through the use of codes, so that only those for whom the information is intended can read and process it.
Text: Cybersecurity in Marvel
*Caesar Cipher (Shift-4): Yuxanoayqnepu ej Iwnrah
*Pigpen Cipher: ᒪᑅ⊔☐⟔ᐯ☐ᒪᐸ⟔ᒥᐳᑅ ᒥ🝕 ⪾ᒧ⟔ᐱ☐ᒷ
*Morse Code: -.-. -.-- -... . .-. ... . -.-. ..- .-. .. - -.-- / .. -. / -- .- .-. ...- . .-..
*RailFence Cipher(Key-6): Civyrtrebuyalec Mrei sn
*Polybius Cipher (Keyword-Smile): 23 55 22 15 44 11 15 23 51 44 13 45 55 13 35 12 21 44 52 15 14
*Playfair Cipher (Keyword-Potato): FVTGSUFDNSKOWLUHTSXCKY
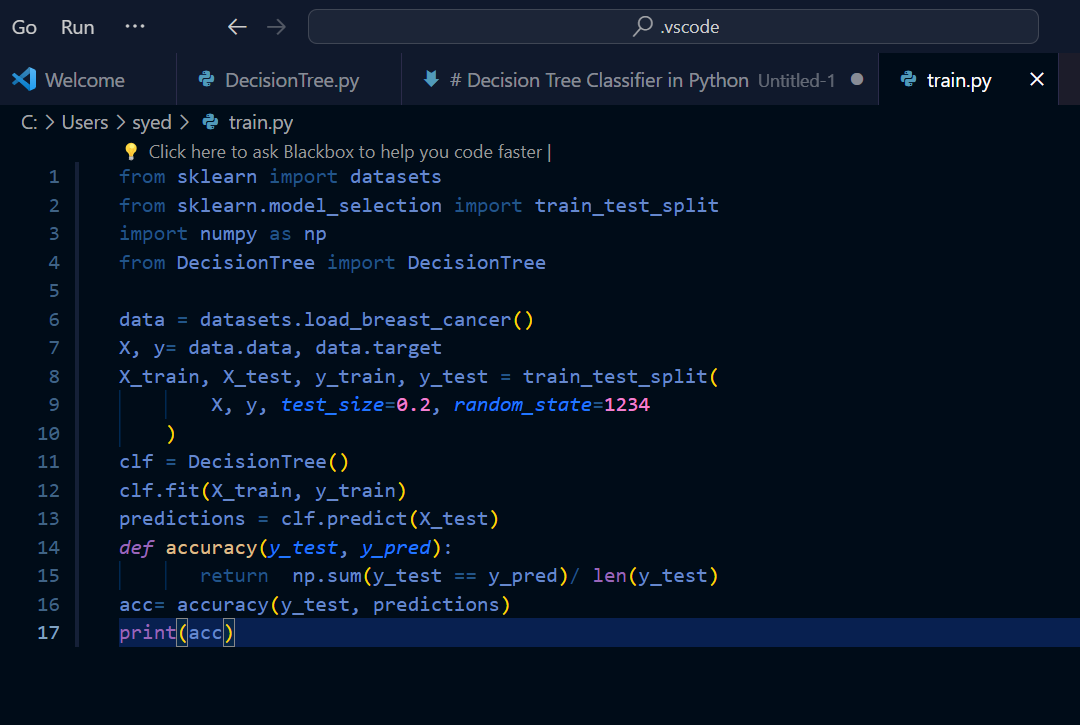
4. Decision Trees (AIML):
Skills and knowledge acquired:
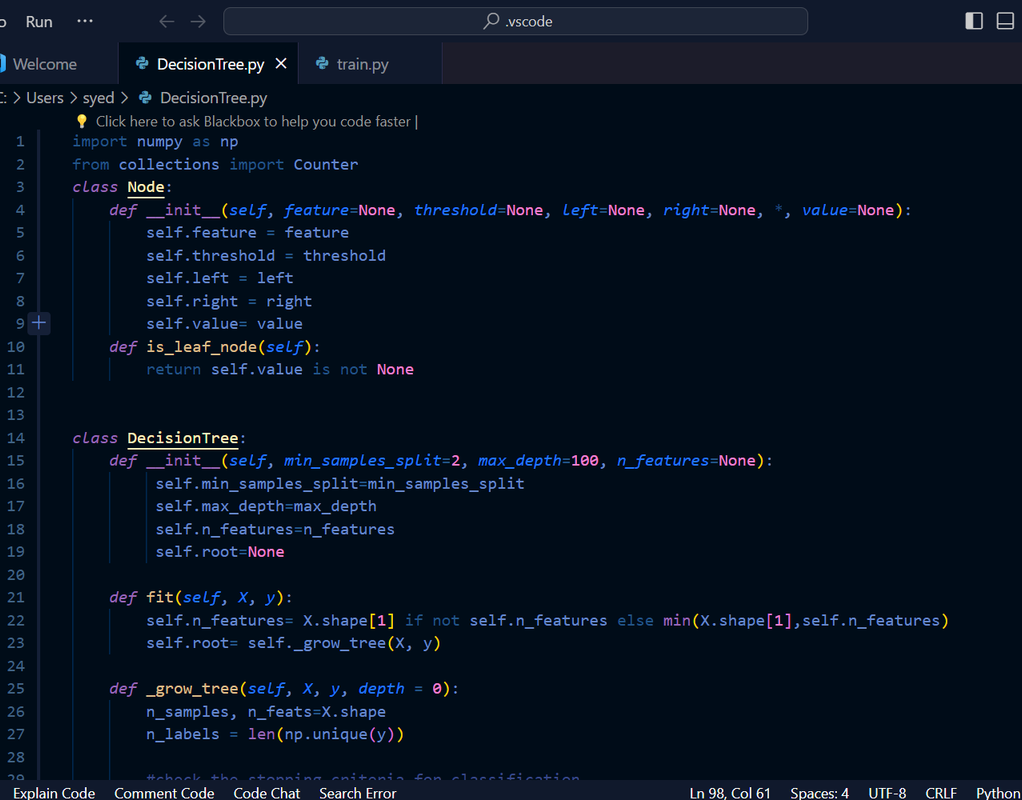
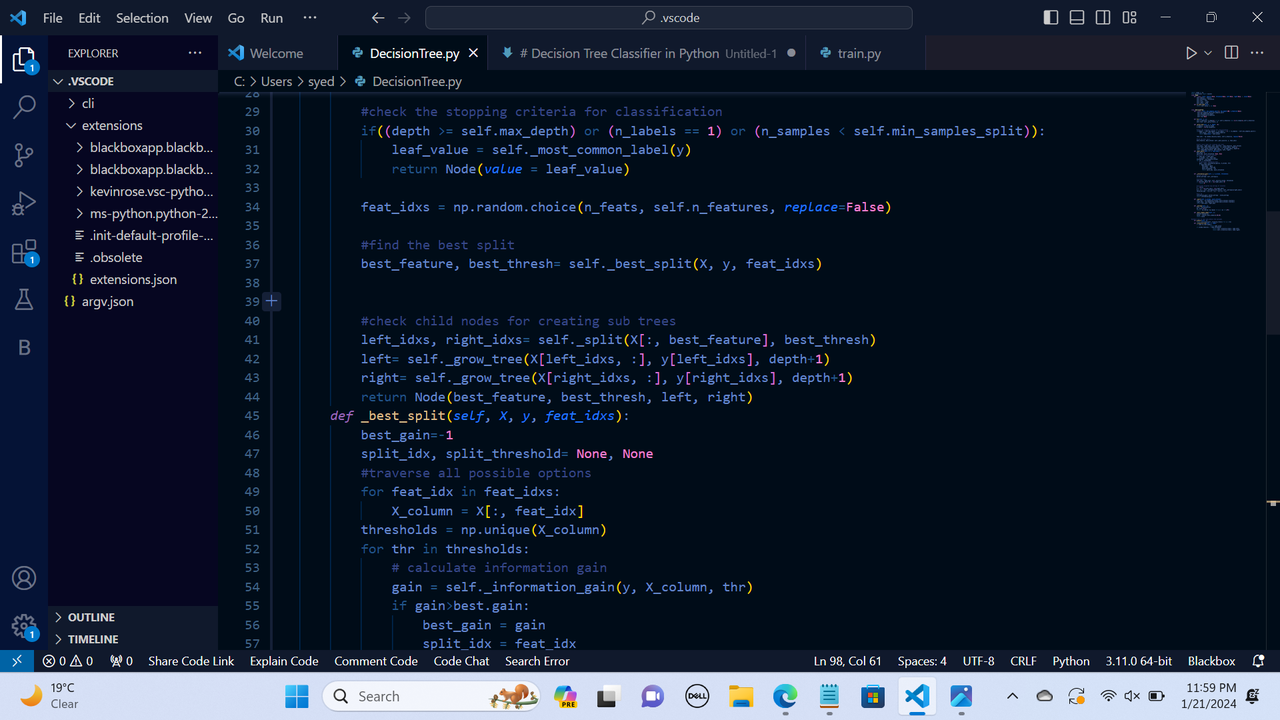
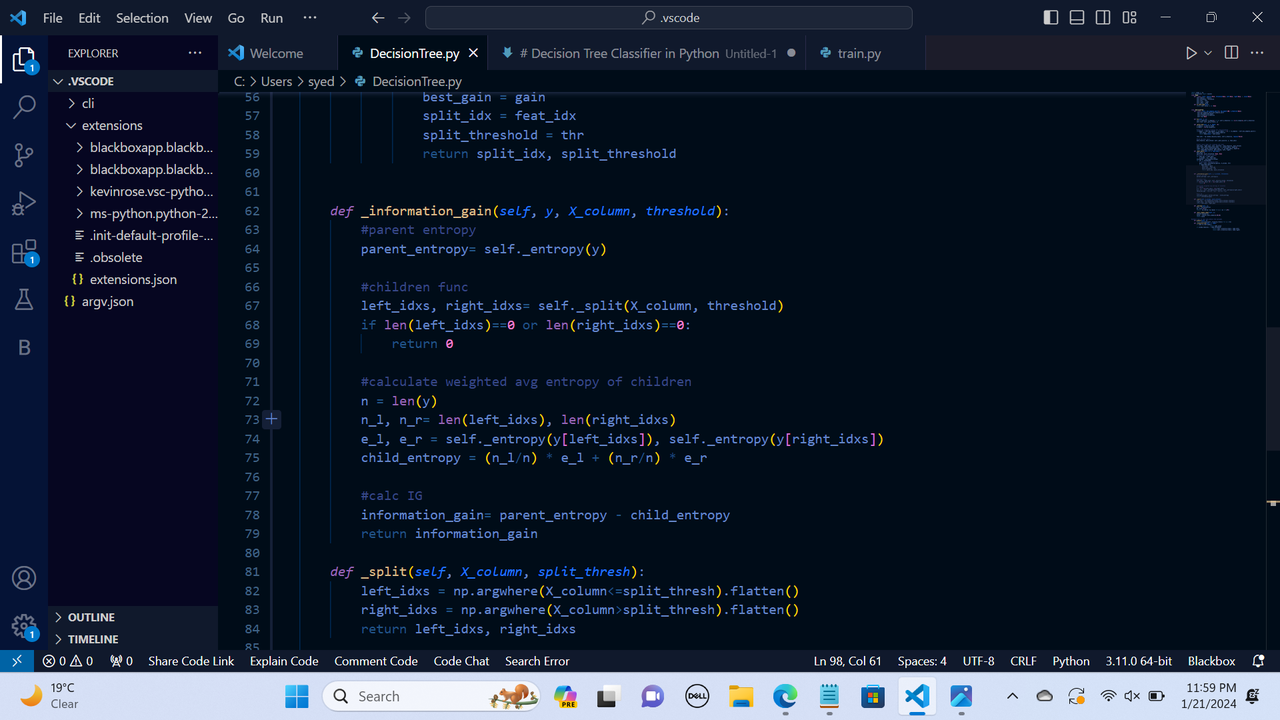
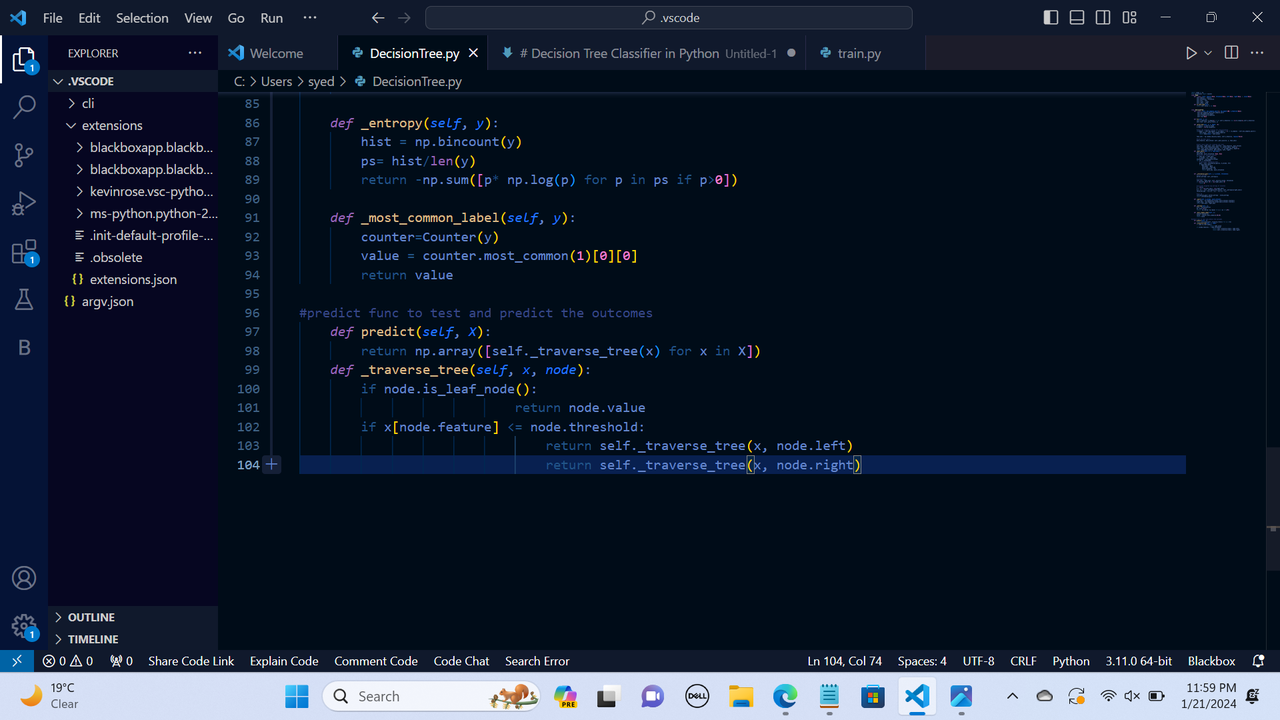
Decision Tree: It is a supervised machine learning algorithm designed for performing regression and classification tasks. It consists of root node, branches, internal nodes, and leaf nodes. It makes use of conditional control statements. It is a hierarchical model algorithm that is used to train datasets and predict potential outcomes, chance events and classification etc. It starts with a root node and ends with a decision made by leaves.
Entropy: It is a measure of randomness or disorder in a dataset.
Information Gain: It is the decrease in entropy after a dataset is split on a particular feature/attribute. IG= Entropy before split- weighted entropy after split.
Splitting Criteria: It is a condition that determines the best possible split of the root node such that the resulting child nodes have lower entropy.
Gini Impurity: It reflects the probability of incorrectly classifying a randomly chosen element in the dataset if it were randomly labeled according to the distribution of classes in the dataset.
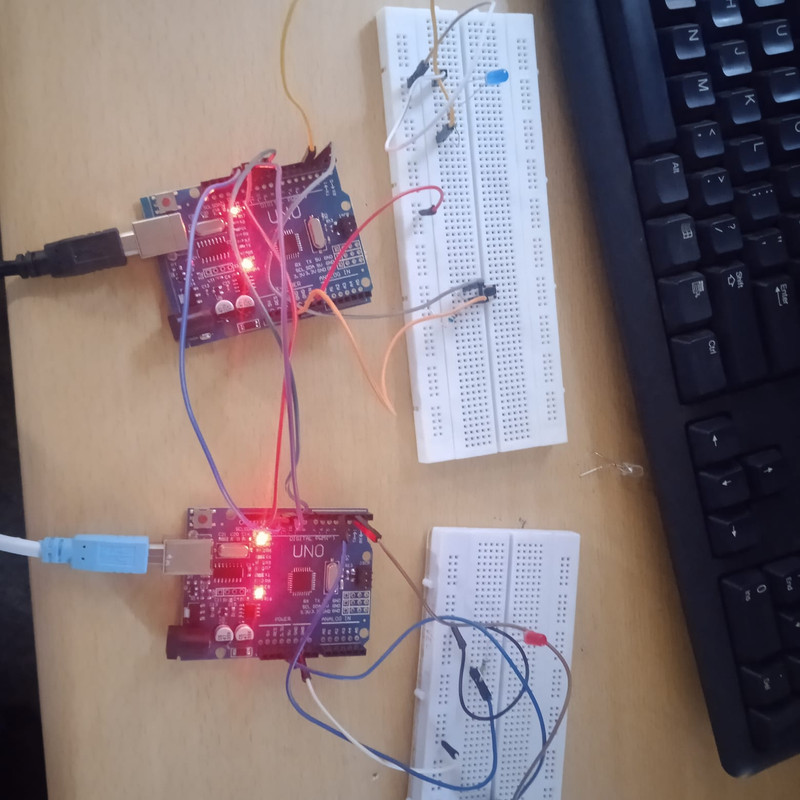
5. SPI Communication:
Skills and knowledge acquired: Learnt to use SPI aka Serial Peripheral Interface with 2 Arduinos as single master and single slave communication. It facilitates duplex communication i.e, data can be transmitted and received simultaneously. It makes use of a synchronous communication channel for which clock signal is required. SPI Protocol operates through 4 lines SCK, MOSI, MISO, SS.
6. I2C Control:
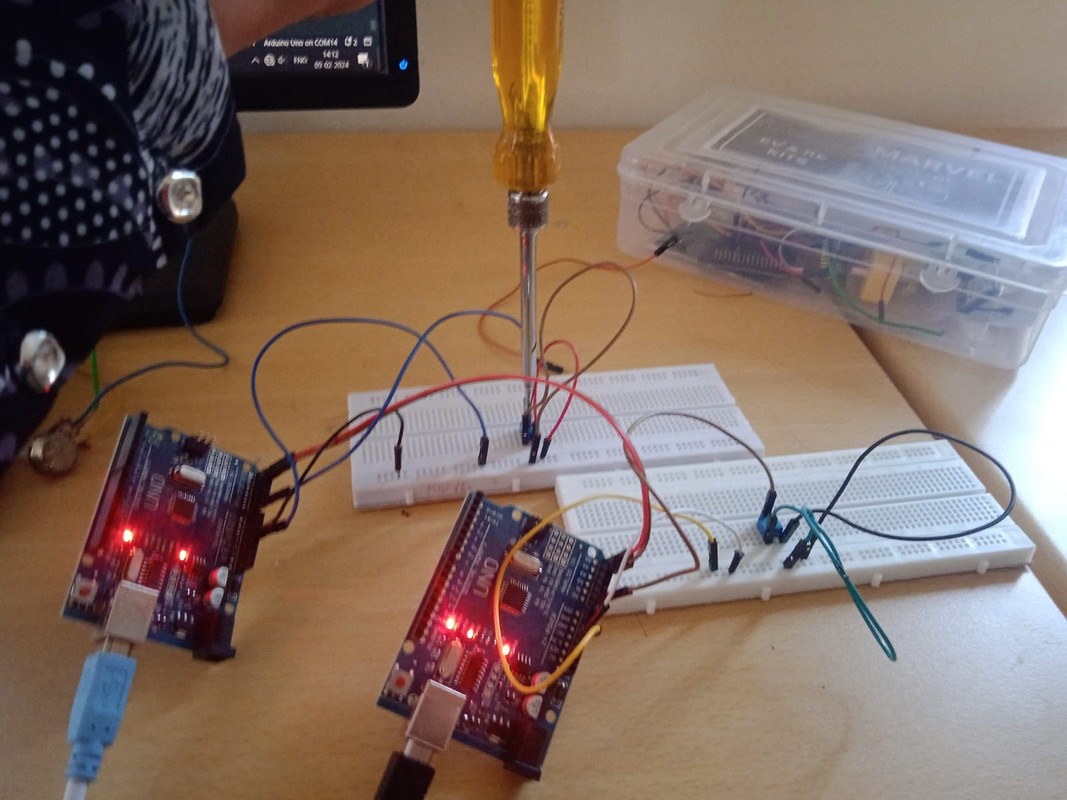
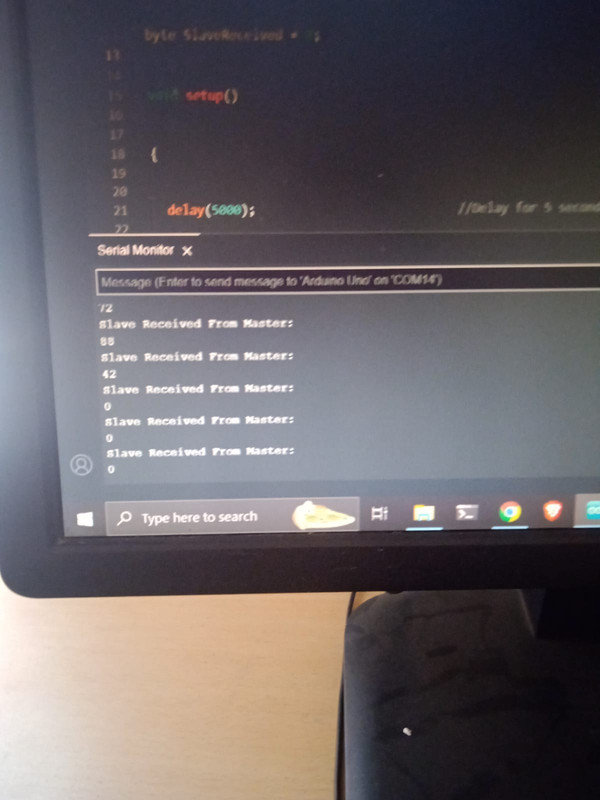
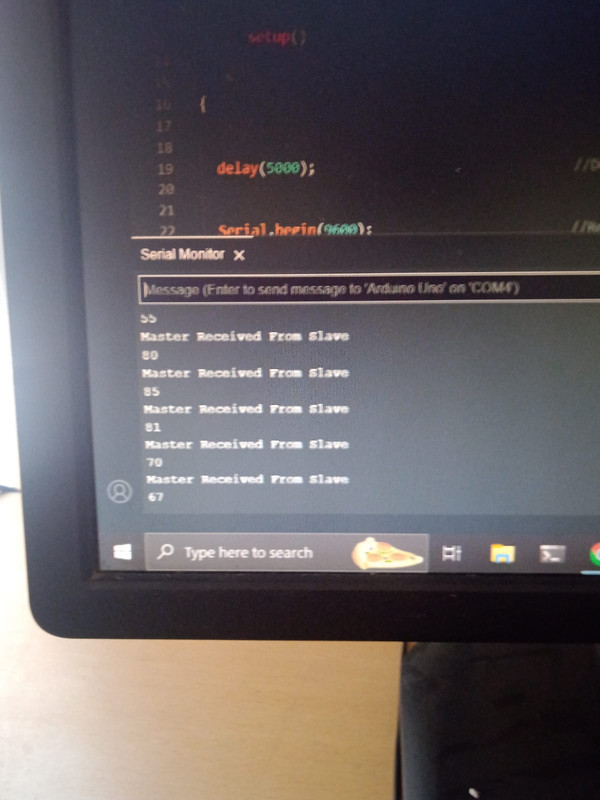
Skills and knowledge acquired: Understanding the basics of the I2C protocol, including how data is transmitted and received between the master and slave devices over a two-wire serial interface. This includes concepts like clock stretching, addressing, and data transmission formats. Setting up the hardware components required for I2C communication, including connecting the Arduinos together via the I2C bus and ensuring proper wiring and component configuration.
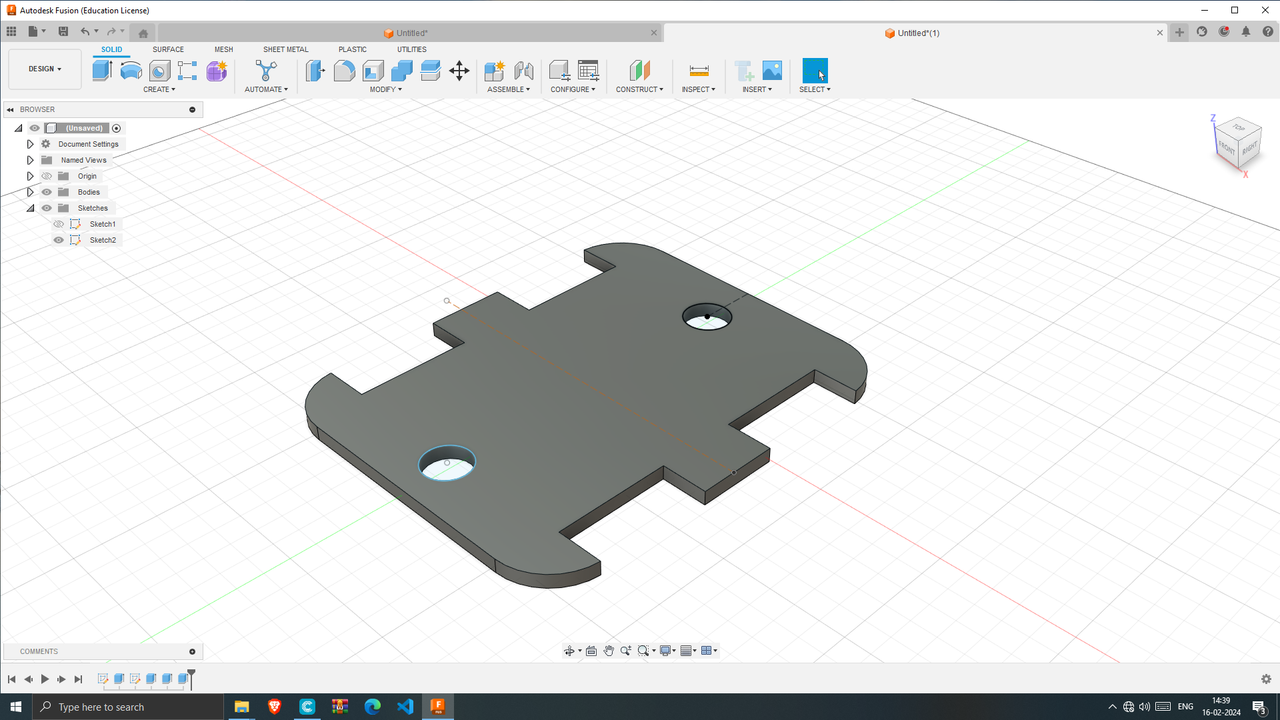
7. Vehicle Chassis Design:
8. Lithium Ion Battery Pack:


Skills & knowledge acquired: Creating a lithium-ion battery pack by soldering four lithium-ion batteries in series which involves connecting the positive terminal of one battery to the negative terminal of the next, forming a continuous chain. This arrangement increases the overall voltage of the battery pack while maintaining the same capacity. Aligning the batteries so that the positive terminal of one battery is connected to the negative terminal of the next, forming a series connection. The total voltage of the battery pack is the sum of the individual battery voltages. For example, if each battery is 3.7 volts, the total pack voltage would be 14.8 volts (3.7V * 4).
9. Battery Management System (BMS):
A Battery Management System (BMS) is an electronic system that manages and protects rechargeable battery packs, such as lithium-ion batteries. It's essential to connect a BMS to lithium-ion batteries connected in series for several reasons:
*Overcharge Protection: Lithium-ion batteries can be damaged if they are overcharged. A BMS monitors the voltage of each cell in the battery pack and prevents overcharging by disconnecting the charging source when the voltage reaches a predetermined threshold.
*Over-discharge Protection: Similarly, over-discharging lithium-ion batteries can lead to irreversible damage. The BMS monitors the voltage of each cell and disconnects the load when the voltage drops below a safe threshold, preventing over-discharge.
*Cell Balancing: During charging and discharging, individual cells within a lithium-ion battery pack may have slightly different capacities or charge levels. Over time, this can lead to cell imbalances, reducing the overall performance and lifespan of the battery pack. A BMS includes circuitry to balance the charge across individual cells, ensuring they are all charged and discharged evenly.
*Temperature Monitoring: Lithium-ion batteries can become damaged or unsafe if they are exposed to extreme temperatures. The BMS monitors the temperature of the battery pack and may take action to prevent charging or discharging if temperatures exceed safe limits.
*Short Circuit Protection: In the event of a short circuit within the battery pack or its external connections, the BMS can quickly disconnect the battery to prevent damage or safety hazards.
*Communication and Monitoring: Advanced BMS systems may include features for communication and monitoring, allowing users to check the status of the battery pack, monitor individual cell voltages, and receive alerts in case of abnormalities.
10. PIR Security System:
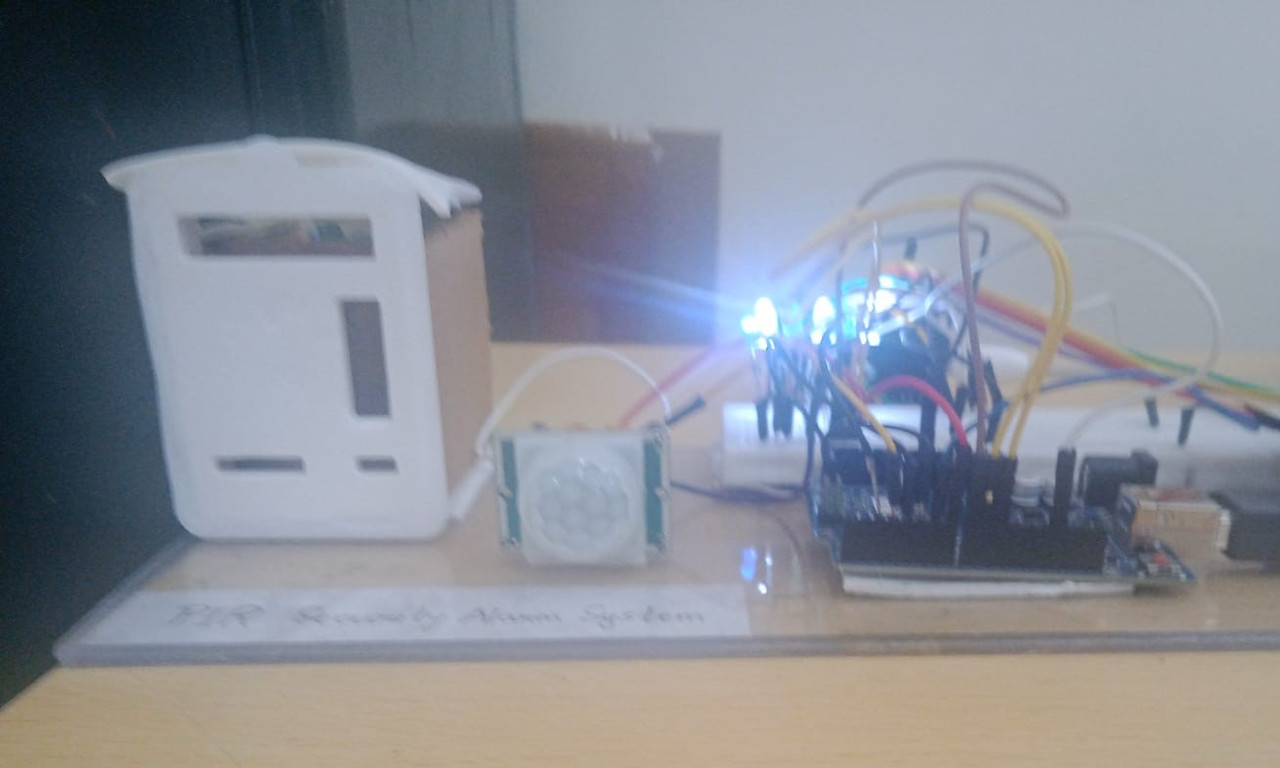
Skills & knowledge acquired: Learning how PIR sensors work and how they detect motion by sensing changes in infrared radiation. Gained knowledge in processing sensor signals and converting them into meaningful data. Understanding how to use conditional statements in the code to respond to specific sensor inputs. Learnt to vary the sensitivity and radius length of the PIR sensor's detection. Learnt about voltage regulation to ensure stable operation.
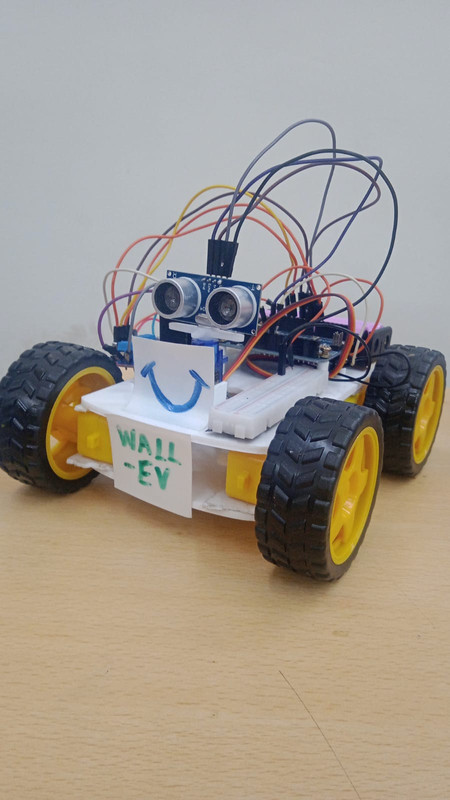
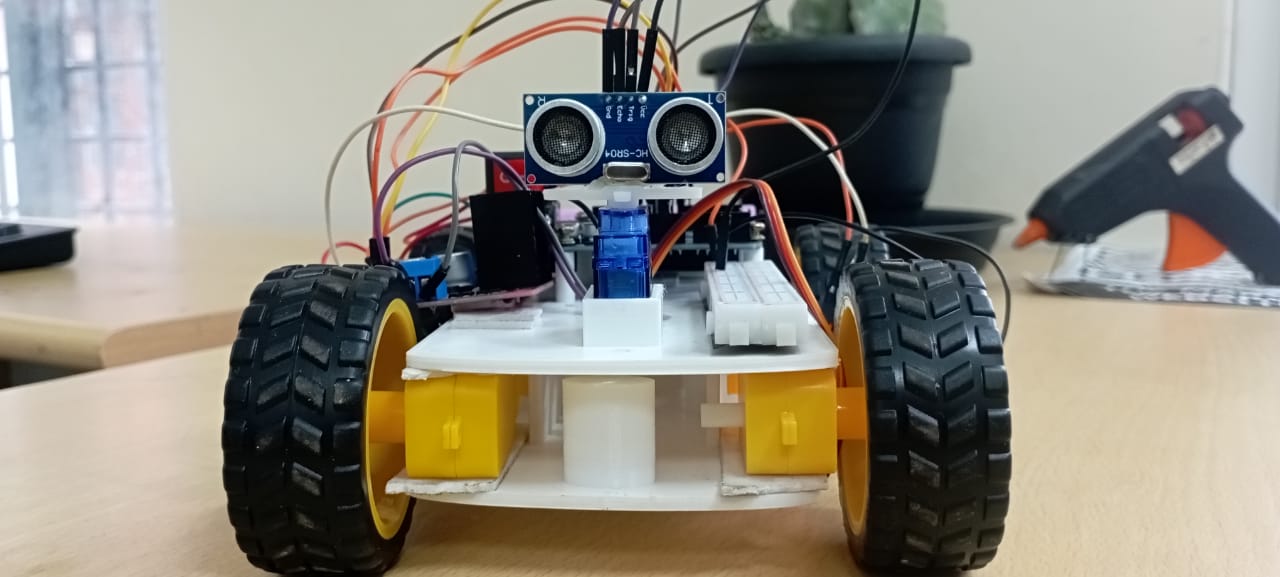
11. Obstacle Detecting Vehicle with Air Quality Monitoring System: