27 / 10 / 2024
TASKS OF LEVEL 2
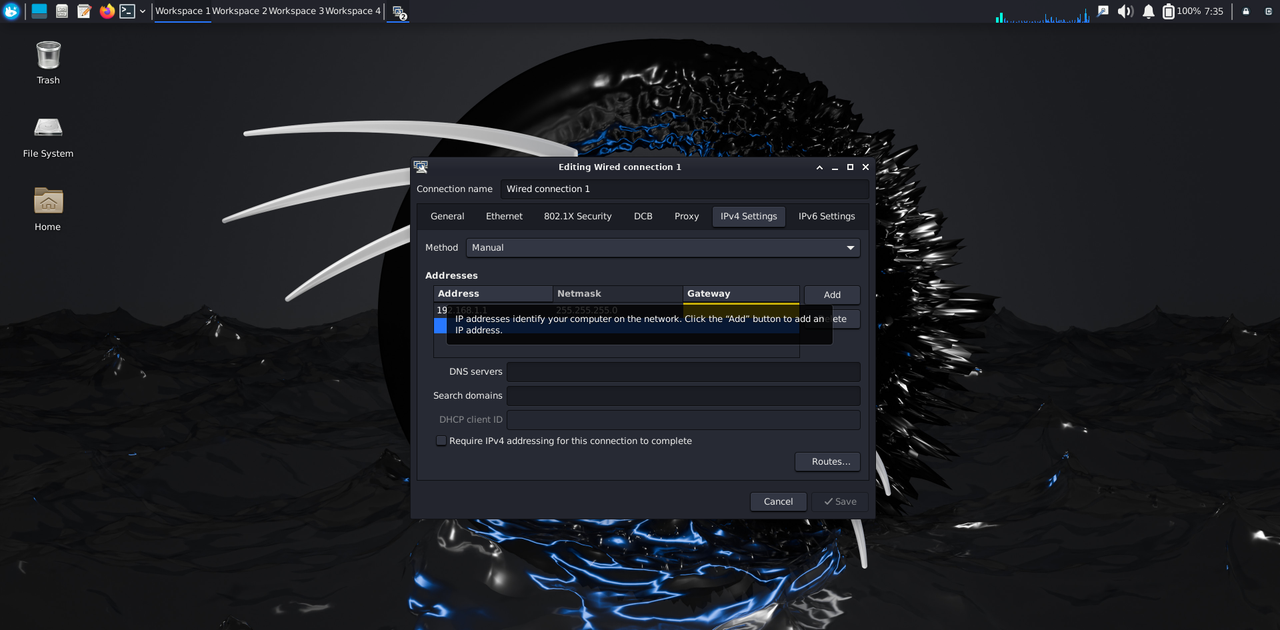
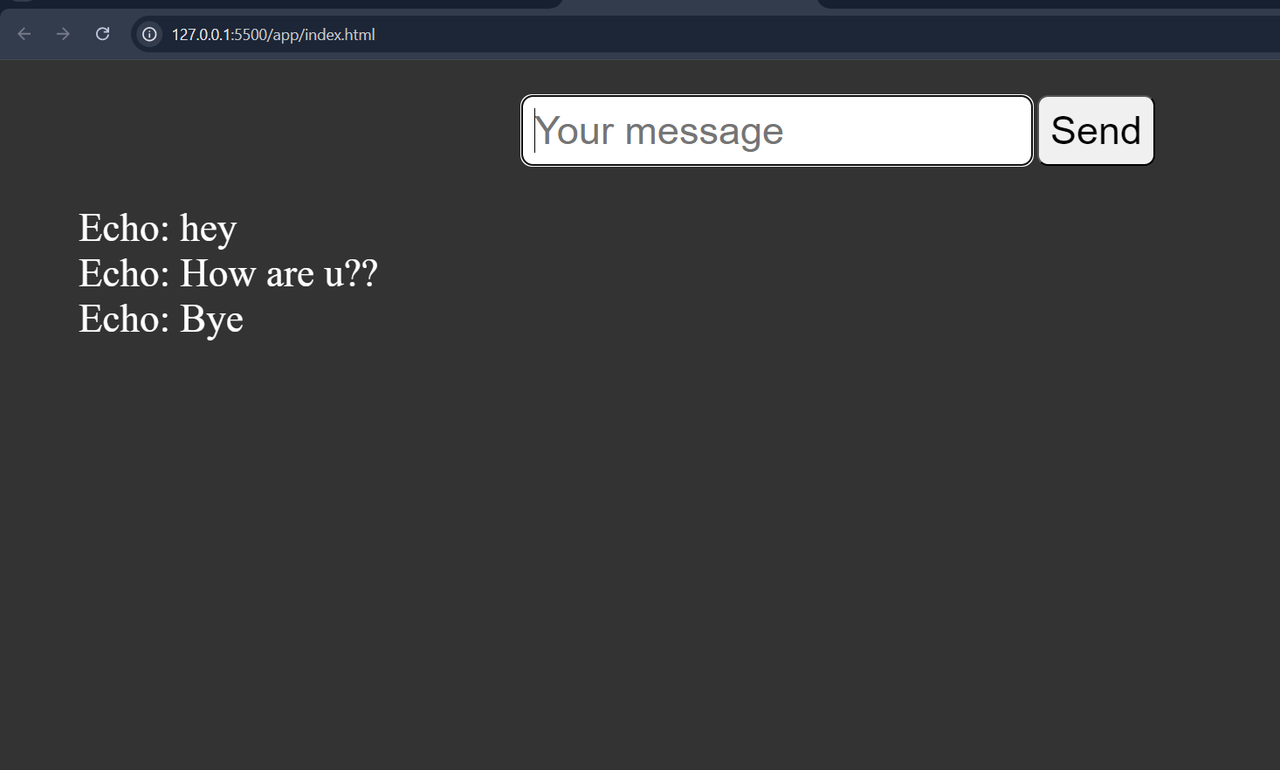
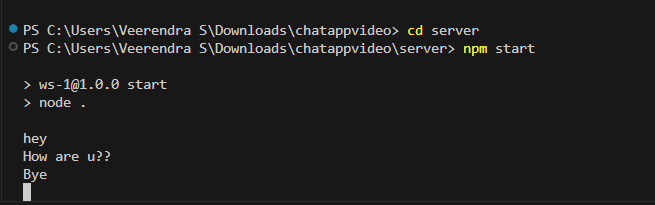
TASK 1: Linux Based Task with Socket.io
Socket.IO is a popular JavaScript library that enables real-time, bidirectional communication between web clients (browsers) and servers. The socket.emit() is used to send data and socket.on() is used to receive data. Repository link : (https://github.com/Veerendras2004/MARVE_LEVEL1/tree/main/socket)
Task 2: Git Bash and GitHub
A command-line tool that provides a Git command-line experience and shell utilities to interact with Git repositories and execute Git commands.
Important Git Commands
# Configure Git
git config --global user.name "Your Name"
git config --global user.email "your.email@example.com"
# Initialize Git Repository
git init
# Clone Repository
git clone
# Check Status
git status
# Add files to staging area
git add # Add a specific file
git add . # Add all files
# Commit Changes
git commit -m "Your commit message"
# Push changes to remote repository
git push origin
# Pull changes from remote repository
git pull
# Check branch
git branch # List branches
git checkout # Switch branch
# Create new branch
git checkout -b
# Merge branches
git merge
# View Commit History
git log
# Remove file from staging area
git reset
# Revert to a specific commit
git reset --hard
# Delete a branch
git branch -d
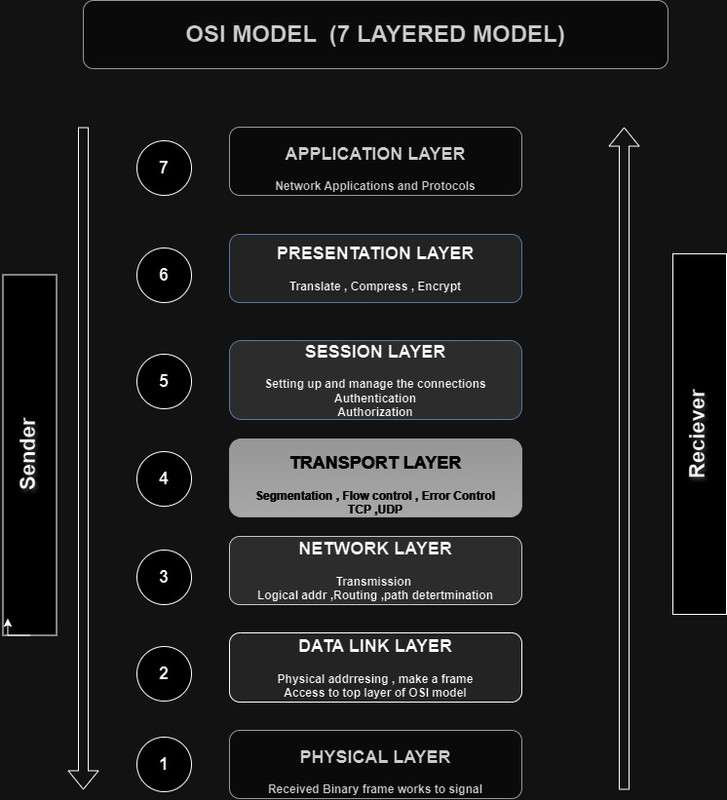
Task 3: OSI MODEL
The OSI (Open Systems Interconnection) model is a conceptual framework that standardizes the functions of a telecommunication or computing system into seven distinct layers, ranging from physical data transmission to application-level interactions.
Task 4:Encryption Techniques
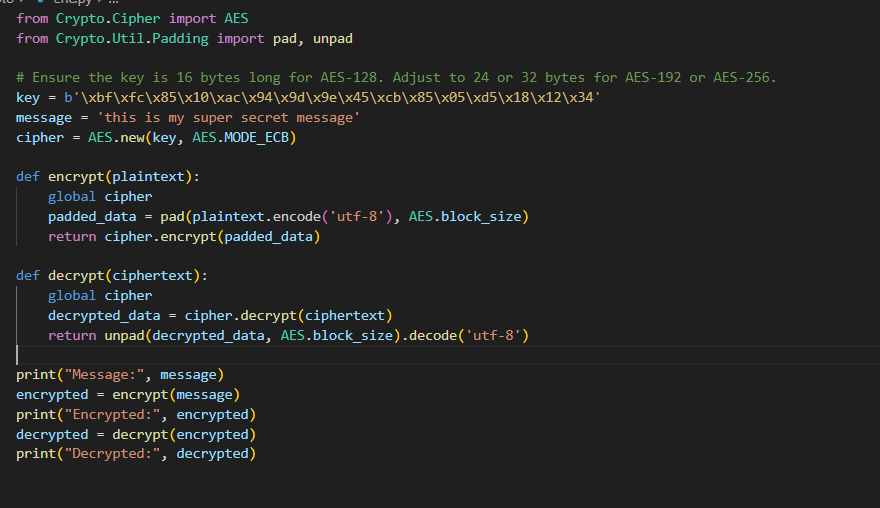
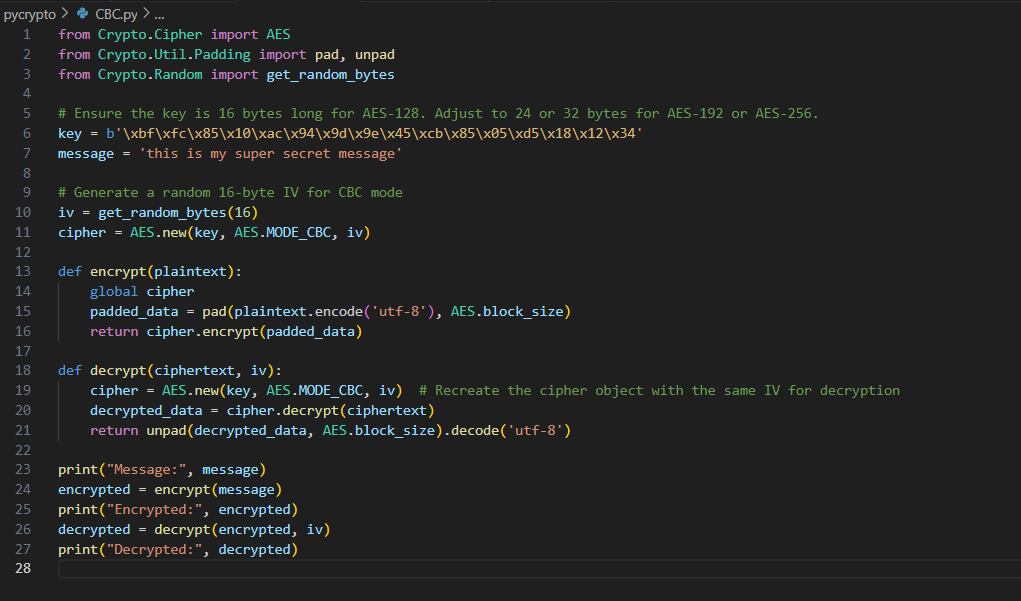
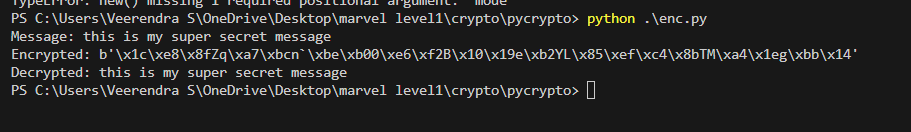
In this task, I developed a basic encryption and decryption program using Python's PyCrypto library, which supports various cryptographic algorithms. I implemented the AES algorithm in two modes: ECB (Electronic Codebook) and CBC (Cipher Block Chaining).
For the ECB mode, I encrypted the plaintext directly, where each block was processed independently. While this approach is faster, it lacks security due to identical plaintext blocks producing identical ciphertext blocks.
In CBC mode, I used an initialization vector (IV) to enhance security. I padded the plaintext to match the required block size before encrypting, ensuring that each block depended on the previous ciphertext. The ciphertext and IV were saved to a file. For decryption, I retrieved the IV and ciphertext, created a cipher with the same key and IV, and decrypted the message, finally unpadding it to restore the original text.
Task 5: IP Addressing and Protocols
WEB SCRAPING
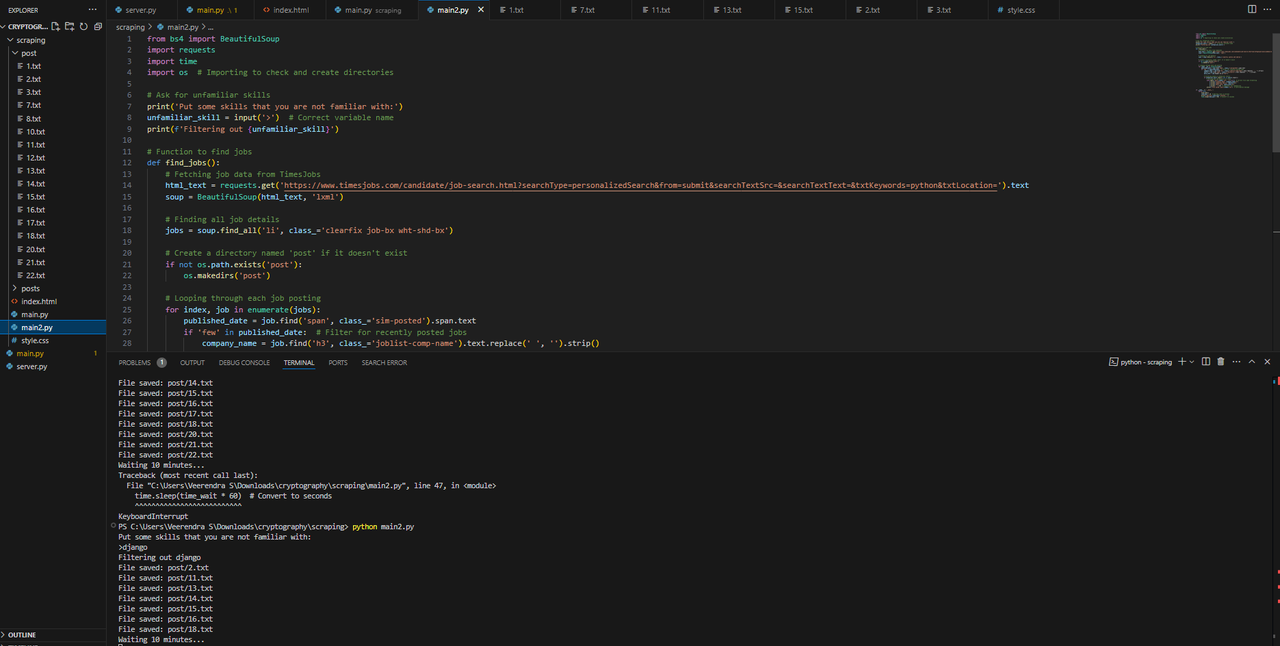
Web scraping with Python and BeautifulSoup involves extracting data from websites by parsing HTML content. BeautifulSoup simplifies the process by providing easy-to-use methods for navigating, searching, and modifying the HTML/XML structure, allowing you to extract the specific information you need.
TASK 6: Kali Linux and SSH
In this task, I installed Kali Linux within Oracle VirtualBox, a powerful tool for virtualization that allows the simultaneous running of multiple operating systems on a single physical machine. Kali Linux is a Debian-based distribution specifically designed for penetration testing and security auditing, making it an ideal choice for cybersecurity tasks.
After successfully setting up the environment, I conducted several Nmap scanning operations. Nmap (Network Mapper) is an open-source tool widely used for network discovery and security auditing.
I performed two types of scans:
TCP Connect Scan (-sT): This scan attempts to establish a full TCP connection with the target host. It is useful for identifying open ports and services running on those ports. While it provides reliable results, it can be easily detected by firewalls and intrusion detection systems.
SYN Scan (-sS): Known as a "stealth" scan, the SYN scan sends SYN packets to the target ports and waits for responses. It is faster and less intrusive than the TCP connect scan, as it does not complete the TCP handshake. This scan is particularly effective for identifying open ports while minimizing the risk of detection.
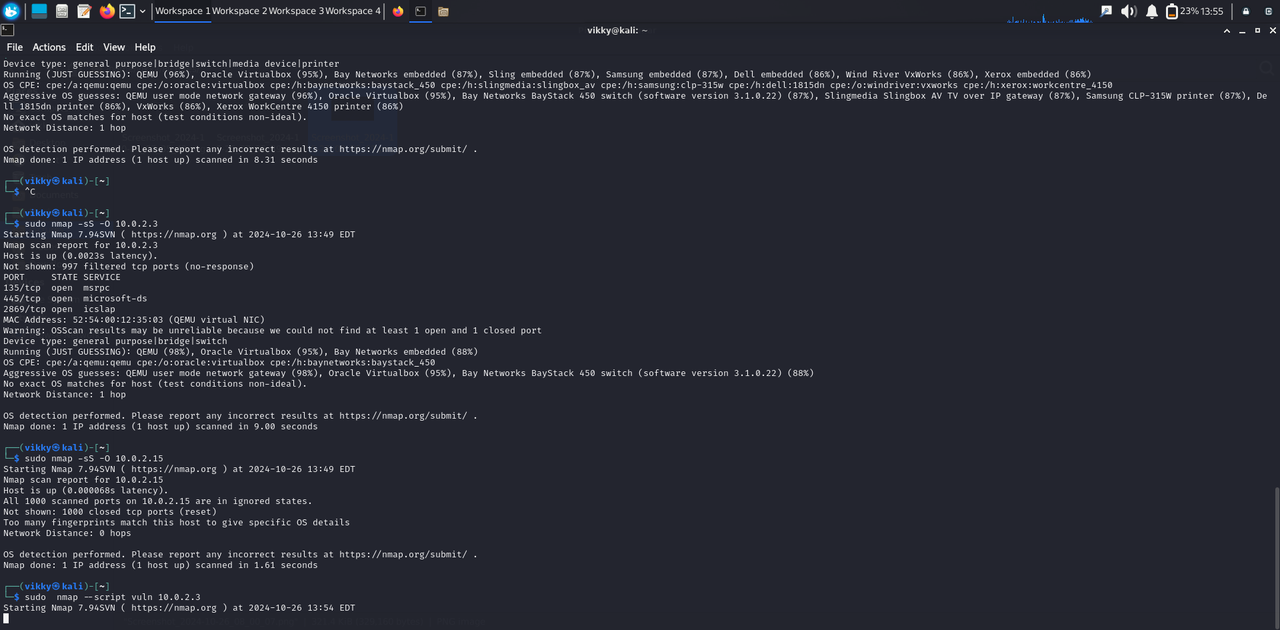
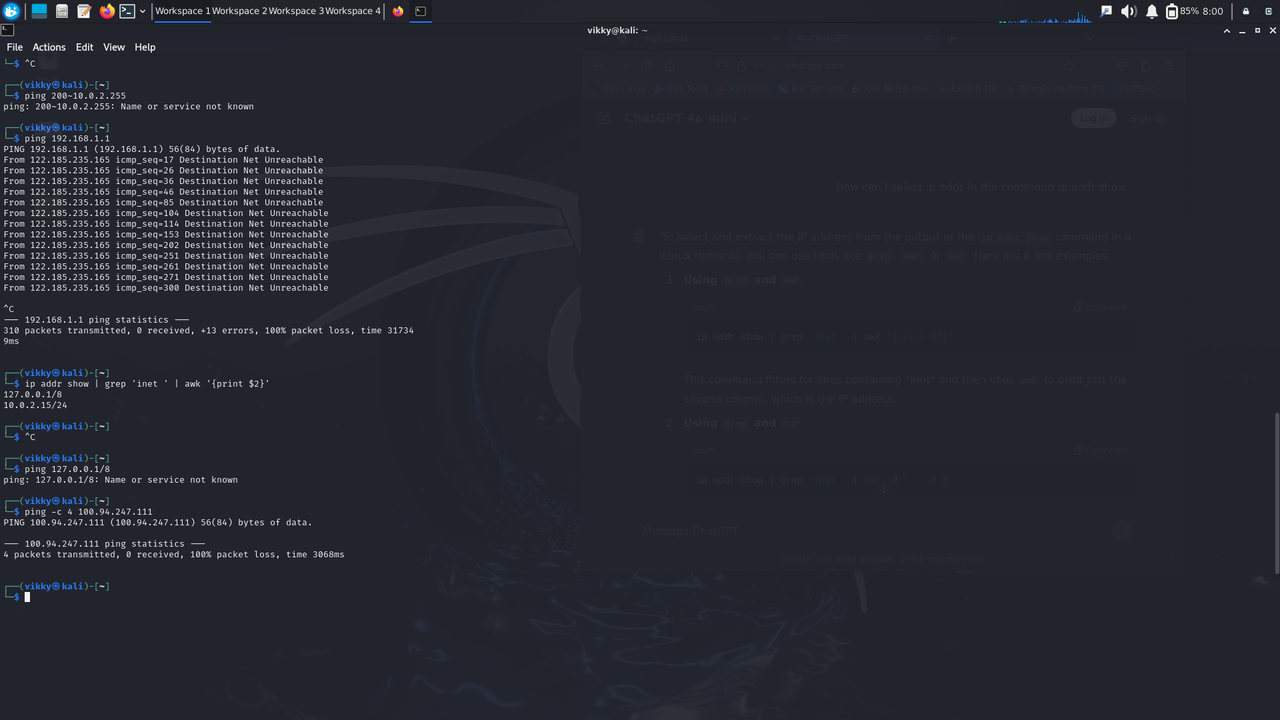
Additionally, I manually changed the IP address of the Kali Linux virtual machine.
I also utilized the ping command to test connectivity with specific IP addresses. This command sends ICMP echo request packets to the target IP, allowing me to verify if the host is reachable
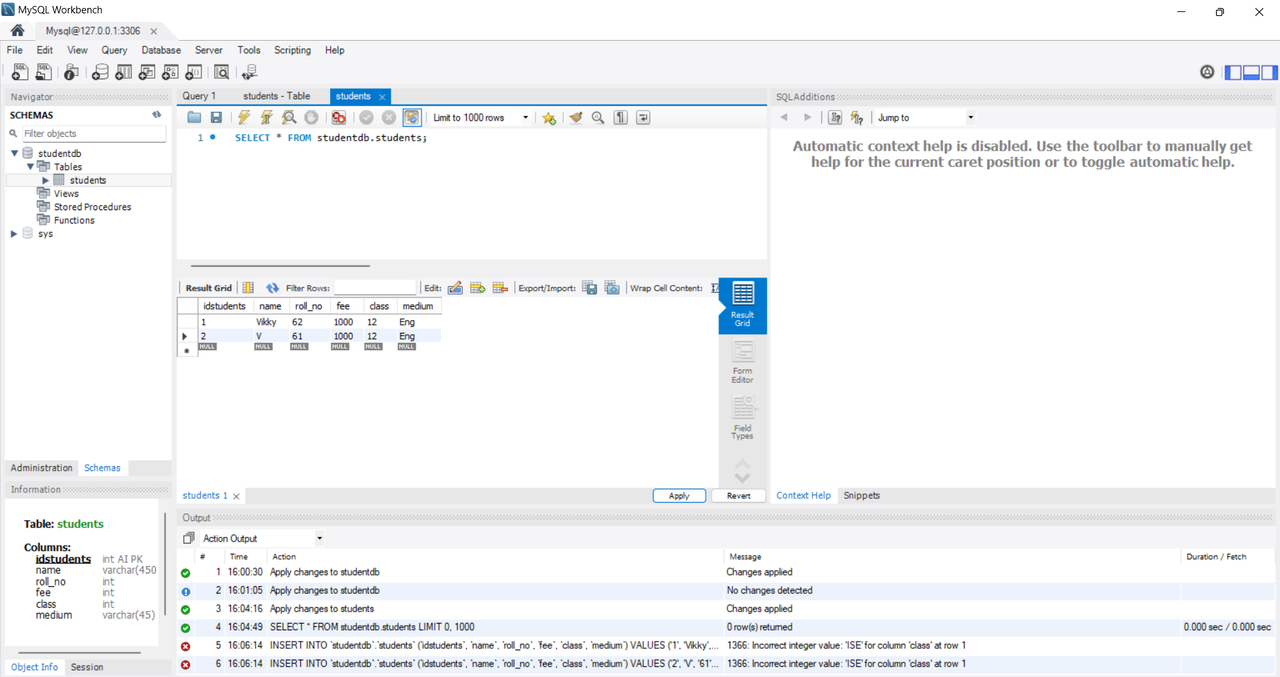
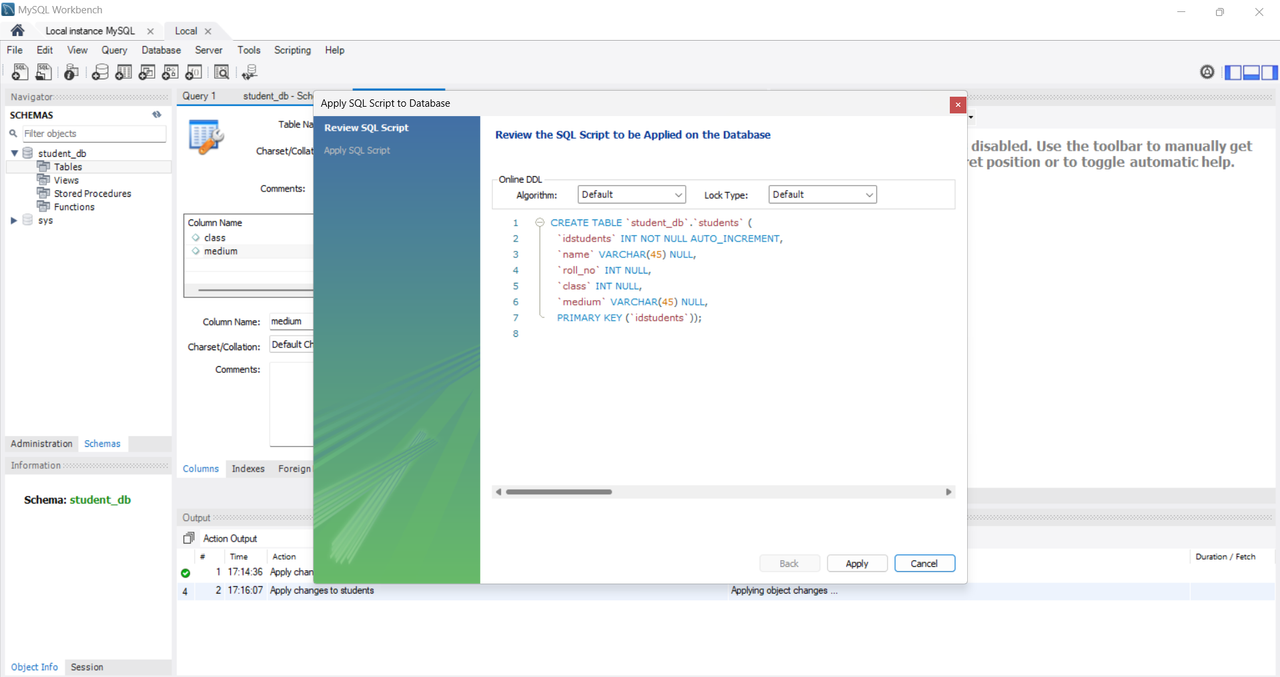
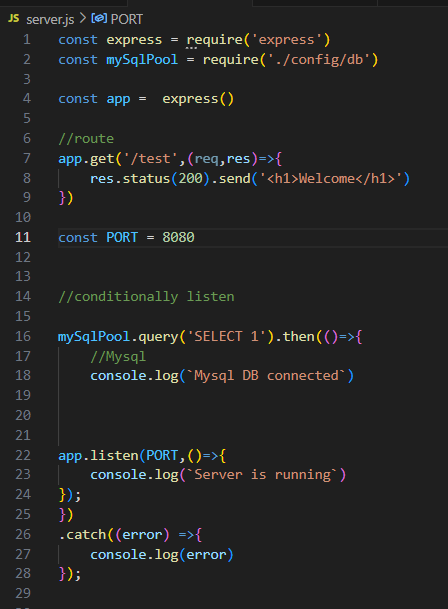
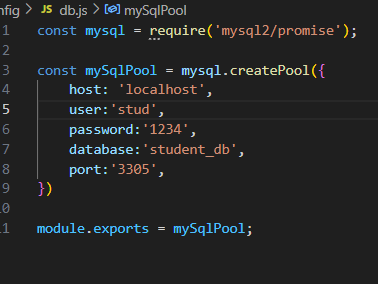
Task 7: Databases
Implementation Overview
In this task, I set up a MySQL database and created a simple CRUD application using Node.js and Express.js. CRUD operations are fundamental for managing data within a database, allowing users to create, read, update, and delete records.
-
Create: To insert new records into a table, the SQL syntax is:
INSERT INTO table_name (column1, column2) VALUES (value1, value2); -
Read: To retrieve data from a table, the syntax is:
SELECT * FROM table_name WHERE condition; -
Update: To modify existing records, use:
UPDATE table_name SET column1 = value1 WHERE condition; -
Delete: To remove records from a table, the syntax is:
DELETE FROM table_name WHERE condition;
Using Postman, I tested these CRUD operations by sending requests to my Express.js server, which interacted with the MySQL database to perform the respective operations. This hands-on experience enhanced my understanding of database management and querying.