Level 1 Tasks Report by Darshan
9 / 3 / 2024
Task 1 - JavaScript
JavaScript is a versatile programming language primarily used for web development. Its specialty lies in its ability to interact with HTML and CSS to create dynamic and interactive web pages. It's an asynchronous, event-driven and dynamically typed scripting language.
Hands-on experience >>>>
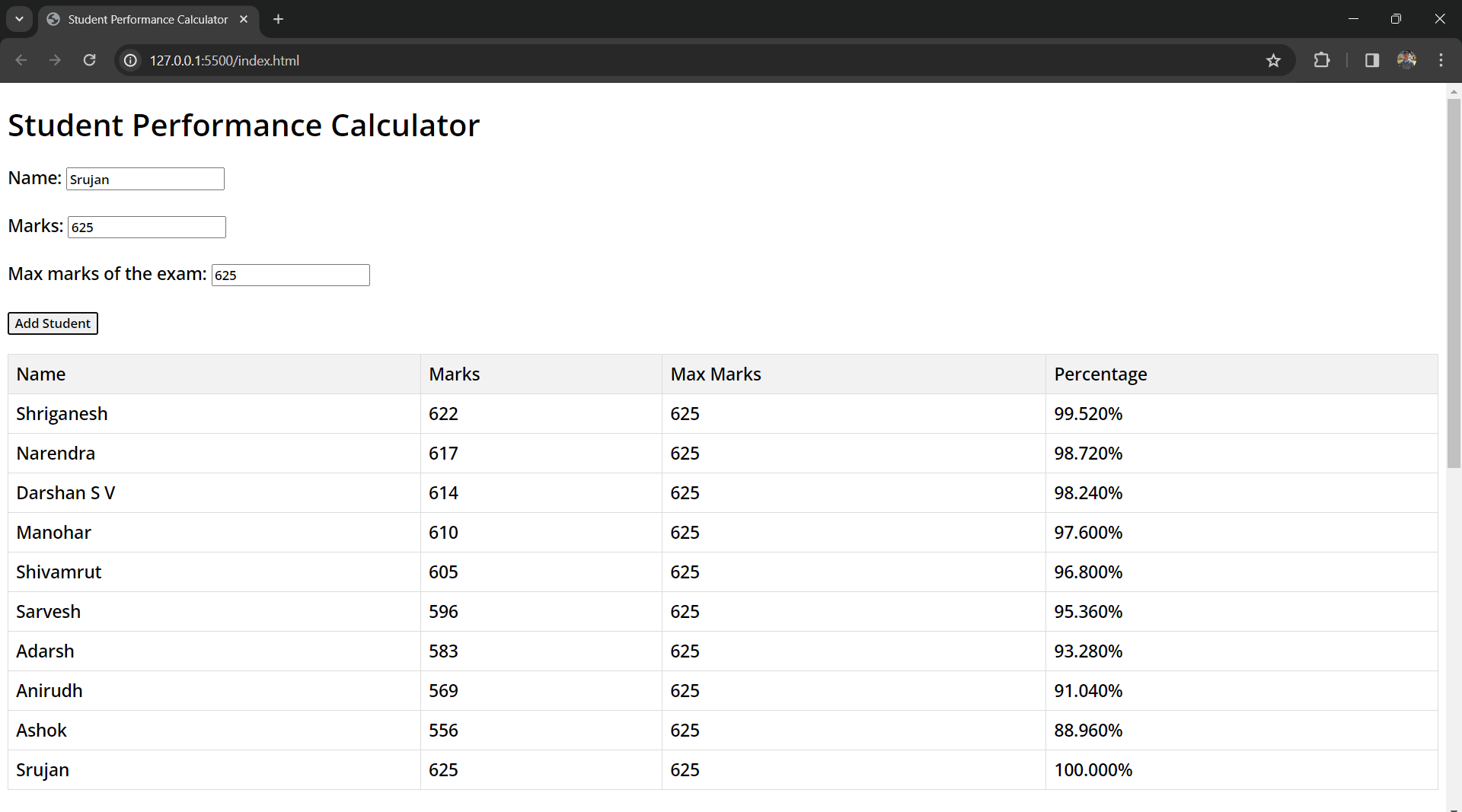
I have created this wonderfull static webpage, Student Performances Calculator using JavaScript. It take name, marks of students through a html form and calculate the following results:
- Percentage of each student.
- Class average.
- Rankings of the students.
Check the full code here (Github repo)
Link to the live webpage
Task 2 - Async JS
Asynchronous JavaScript refers to a programming pattern used in JavaScript to handle operations that might take some time to complete, such as fetching data from a server or performing calculations. It does not block the execution of other code. This allows JavaScript to perform multiple tasks simultaneously without waiting for one operation to finish before starting another.
A Callback is a function that is passed as an argument to another function and is executed later, typically after the completion of an asynchronous operation or some other event.
Hands-on experience >>>>
I have implemented a small callback based website that displays the steps to bake a cake.
Crux Code
const displayStep = (step, callback) => {
const recipeStepsElement = document.getElementById("recipe-steps");
const stepDiv = document.createElement("div");
stepDiv.textContent = step;
recipeStepsElement.appendChild(stepDiv);
setTimeout(callback, 2000);
};
const startRecipe = () => {
let index = 0;
const displayNextStep = () => {
if (index < recipeSteps.length) {
const step = recipeSteps[index];
displayStep(step, () => {
autoScrollDown(displayNextStep);
});
index++;
} else {
alert("Recipe completed!");
}
};
displayNextStep();
};
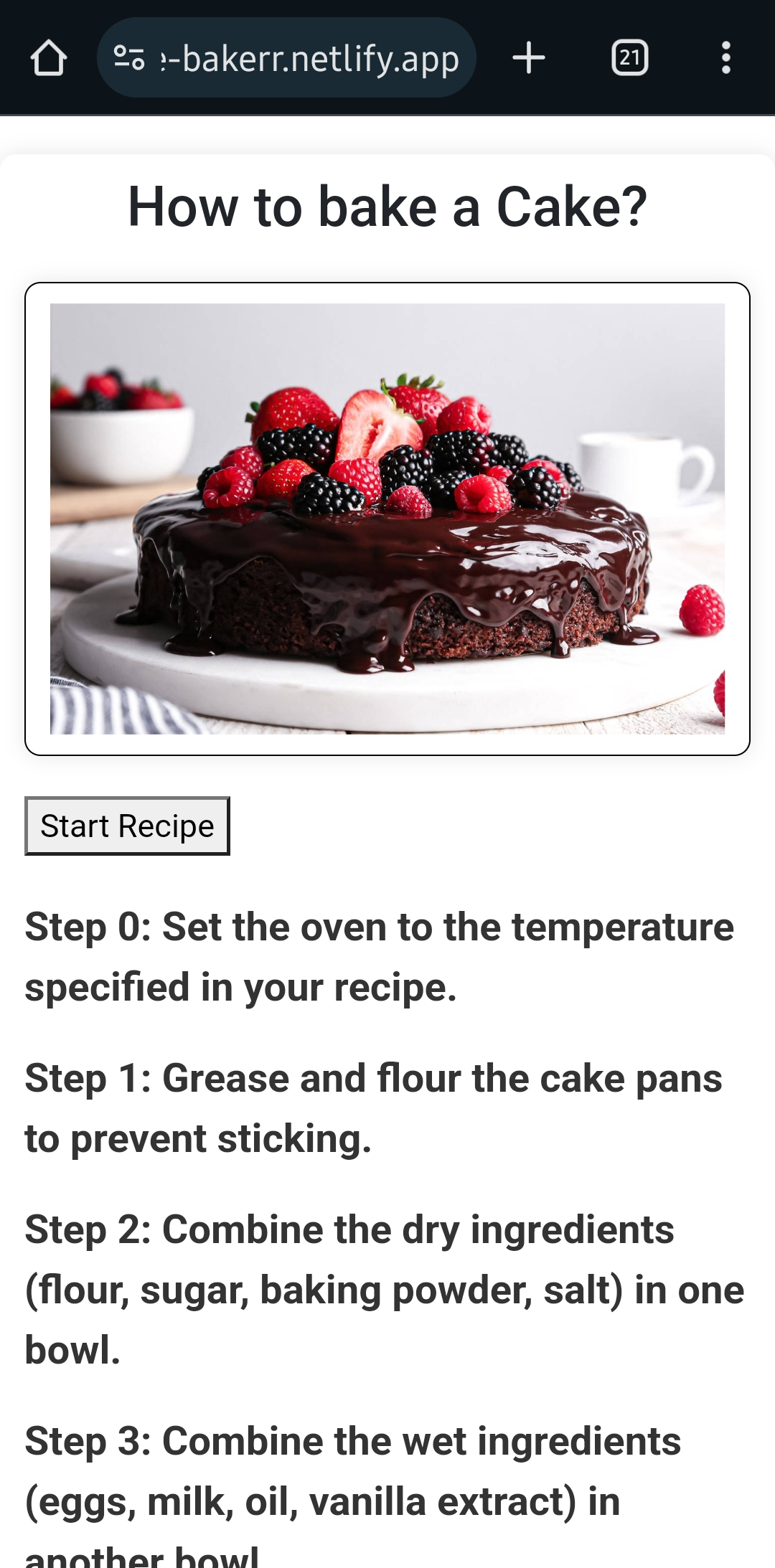
Link to the live webpage
Task 3 - Promises
 Objective of this task:
Objective of this task:
To implement the previous recipe program with promises and learn the potential benefits and improvements of using the promises.
Promises in JavaScript provide a cleaner and more structured way to handle asynchronous operations, providing better readability, error handling, and control flow compared to traditional callback-based approaches. They represent the eventual completion or failure of an asynchronous operation and allow you to attach callbacks to handle the result once it's available.
A promise can be in one of three states: pending, fulfilled, or rejected. When a promise is created, it's in the pending state. It transitions to either fulfilled (resolved successfully) or rejected (encountered an error) based on the outcome of the asynchronous operation.
Crux Code
const displayStep = (step) => {
return new Promise((resolve) => {
const recipeStepsElement = document.getElementById("recipe-steps");
const stepDiv = document.createElement("div");
stepDiv.textContent = step;
recipeStepsElement.appendChild(stepDiv);
setTimeout(resolve, 2000);
});
};
const startRecipe = () => {
const stepsPromises = recipeSteps.map((step) => displayStep(step));
Promise.all(stepsPromises)
.then(() => {
alert("Recipe completed!");
})
.catch((error) => {
console.error("Error occurred:", error);
});
};
Check the full code here (Github repo)
Link to the live webpage
Task 4: Get familiar with the command line on ubuntu:
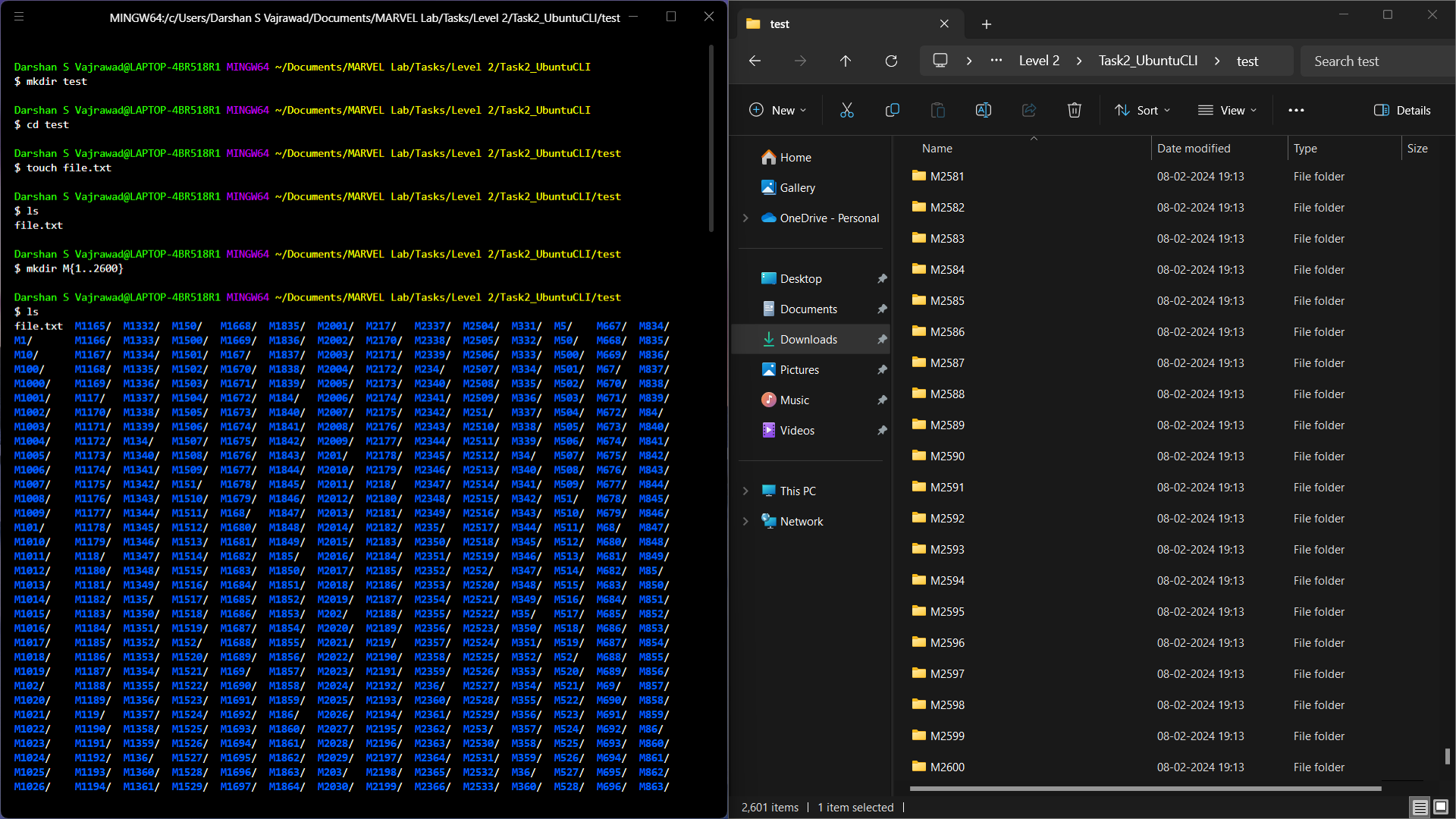
- Create a folder named test.
- cd into that folder.
- Create a blank file without using any text editor.
- List the files in that folder.
- Create 2600 folders in this folder where each folder is named M90.
for i in {1..2600}; do
mkdir "M$i"
done
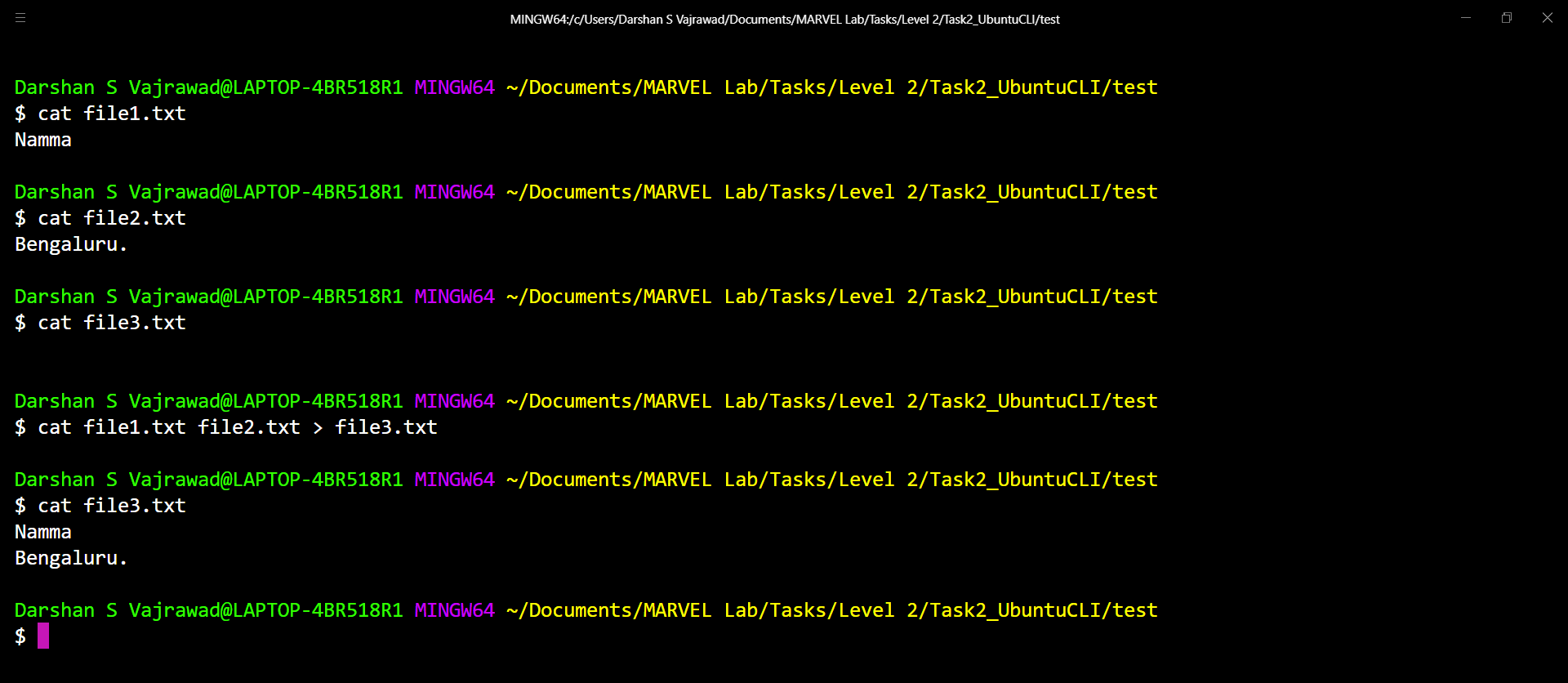
- Concatenate two text files containing any random text and display them on the terminal.
echo "Random Text File 1" > file1.txt
echo "Random Text File 2" > file2.txt
cat file1.txt file2.txt
Task 5 - VI
Vi is a powerful and ubiquitous text editor that has been a staple in the UNIX and Linux environments. Known for its efficiency and versatility, Vi provides users with a minimalist yet highly customizable interface for editing text files directly within the terminal.
Key features of Vi include its modal editing system, which allows users to switch between different modes for tasks such as inserting text, navigating, and making edits.
Hands on experience >>>>>
I learnt to edited text files in VI text-editor in Linux systems. I have edited a complete text file in VI, the images and link to the repo is given below.
Task 6 - Linux Continued
Objectives of this task:
- Basics of regex and piping.
- Learn how grep works.
- Use grep to extract login times within a date/time range from the login logs using the 'last' command.
- Pipe this information into a text file and put it into a folder named logs. Zip this folder using gzip and tar.
Hands on experience >>>>>
To create an empty folder named logs and an empty file.
mkdir logs
cd logs/
touch task6.txt
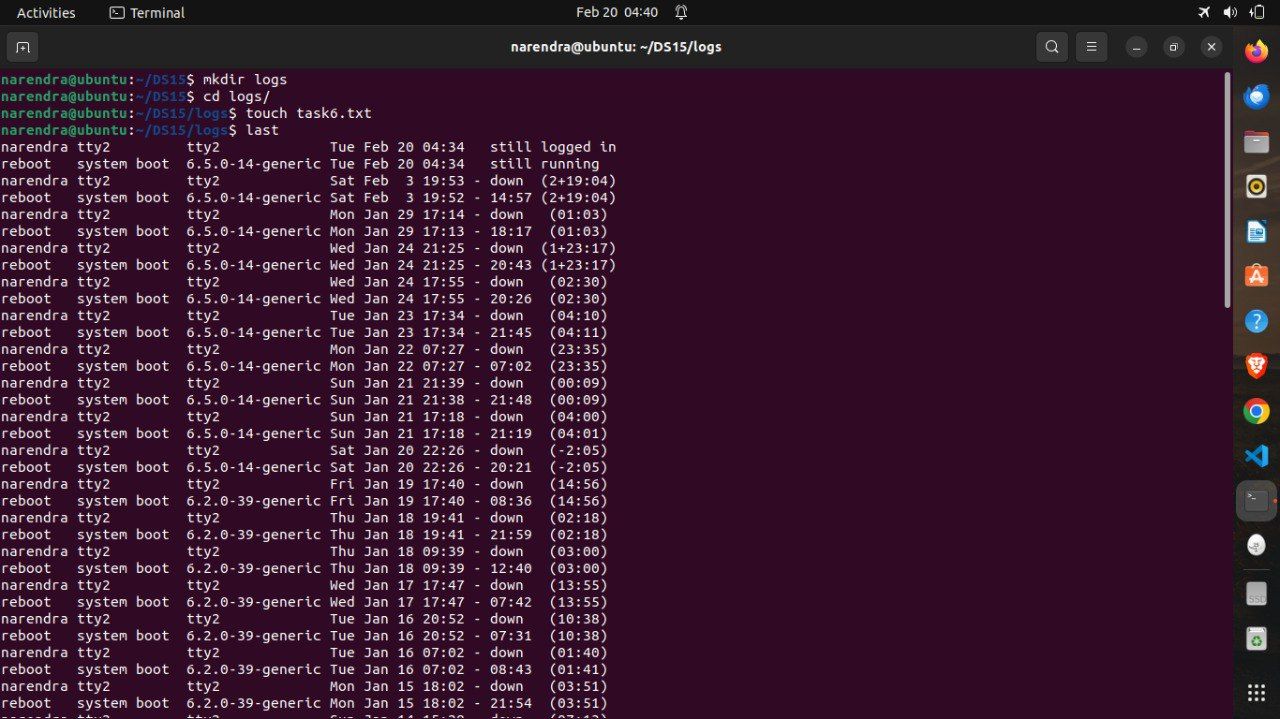
last | grep '.2[0-9] 1[3-9]:.' > task6.txt
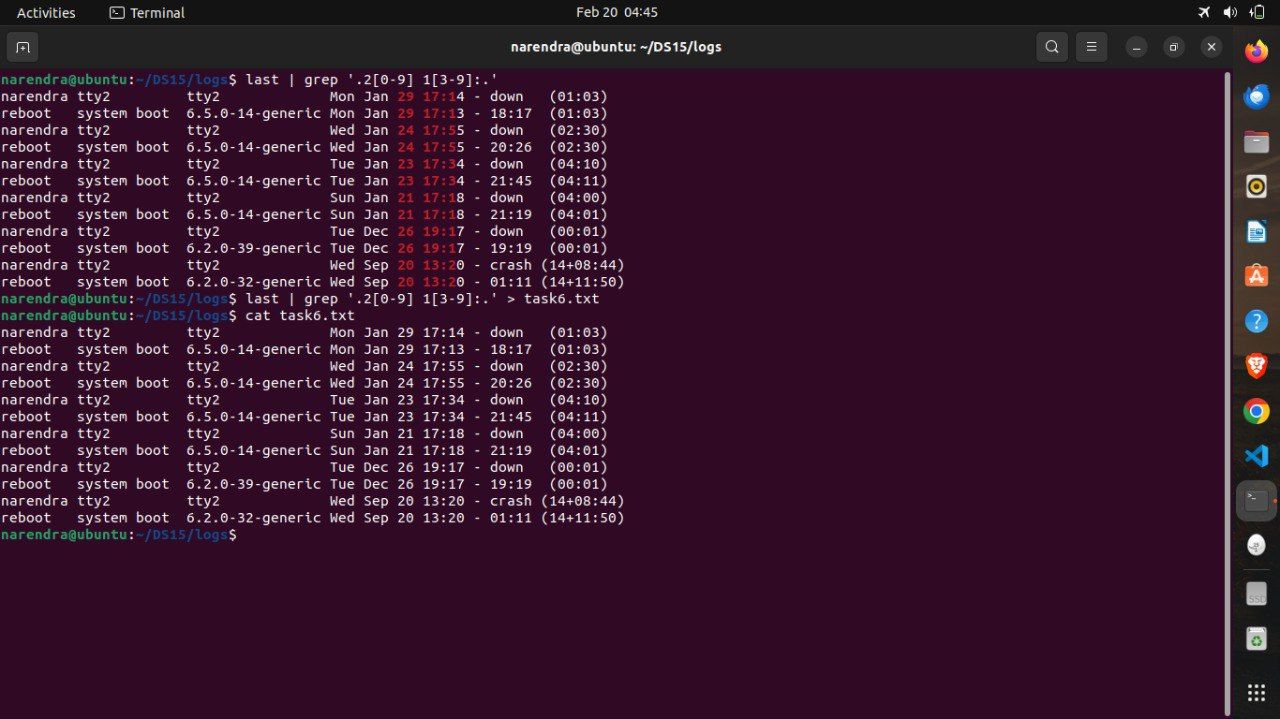
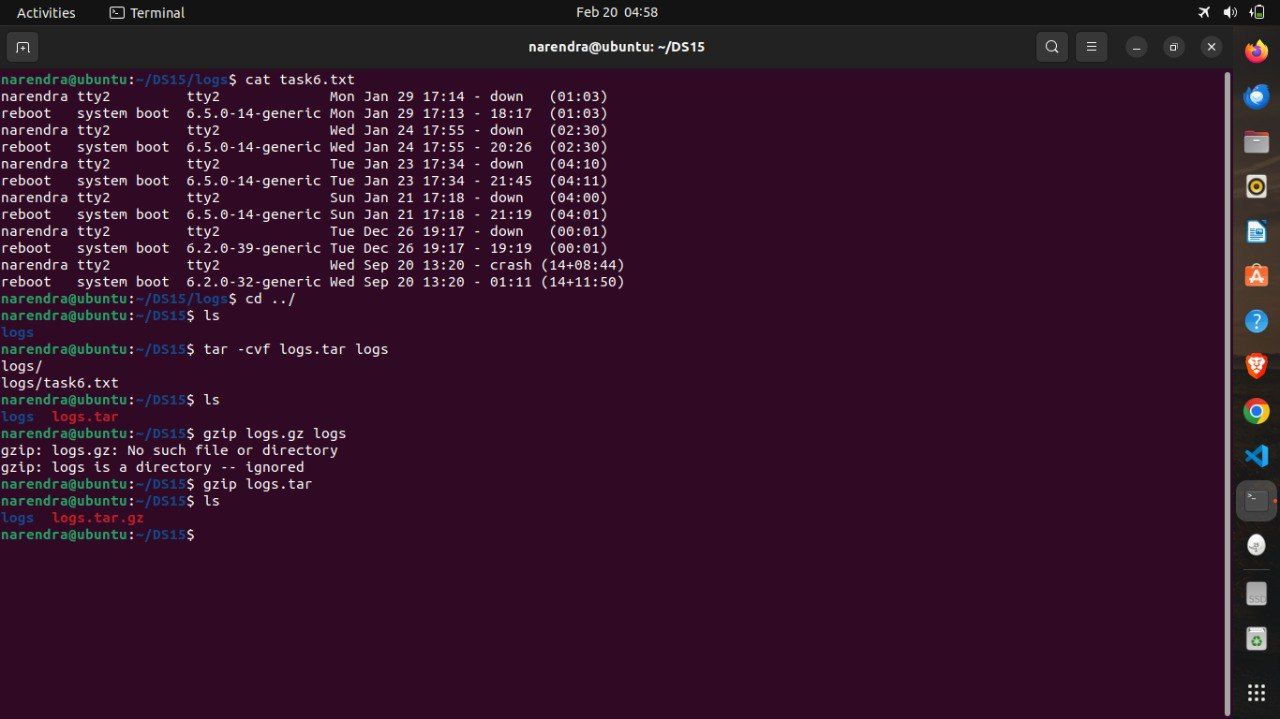
tar -cvf logs.tar logs
gzip logs.tar
Task 7 - Introduction to Cloud Computing
Cloud Computing refers to data and applications being stored and run on the cloud rather than on our local computer.
The cloud is a place where large numbers of servers are stored and kept functional so as to provide services like running applications, storing data, data processing and web hosting.
A server is simply a computer with high end configuration that is kept functional all time.
Top players in the cloud industry
- Amazon Web Services [AWS]
- Microsoft Azure
- Google Cloud Platform [GCP]
- Alibaba
- IBM
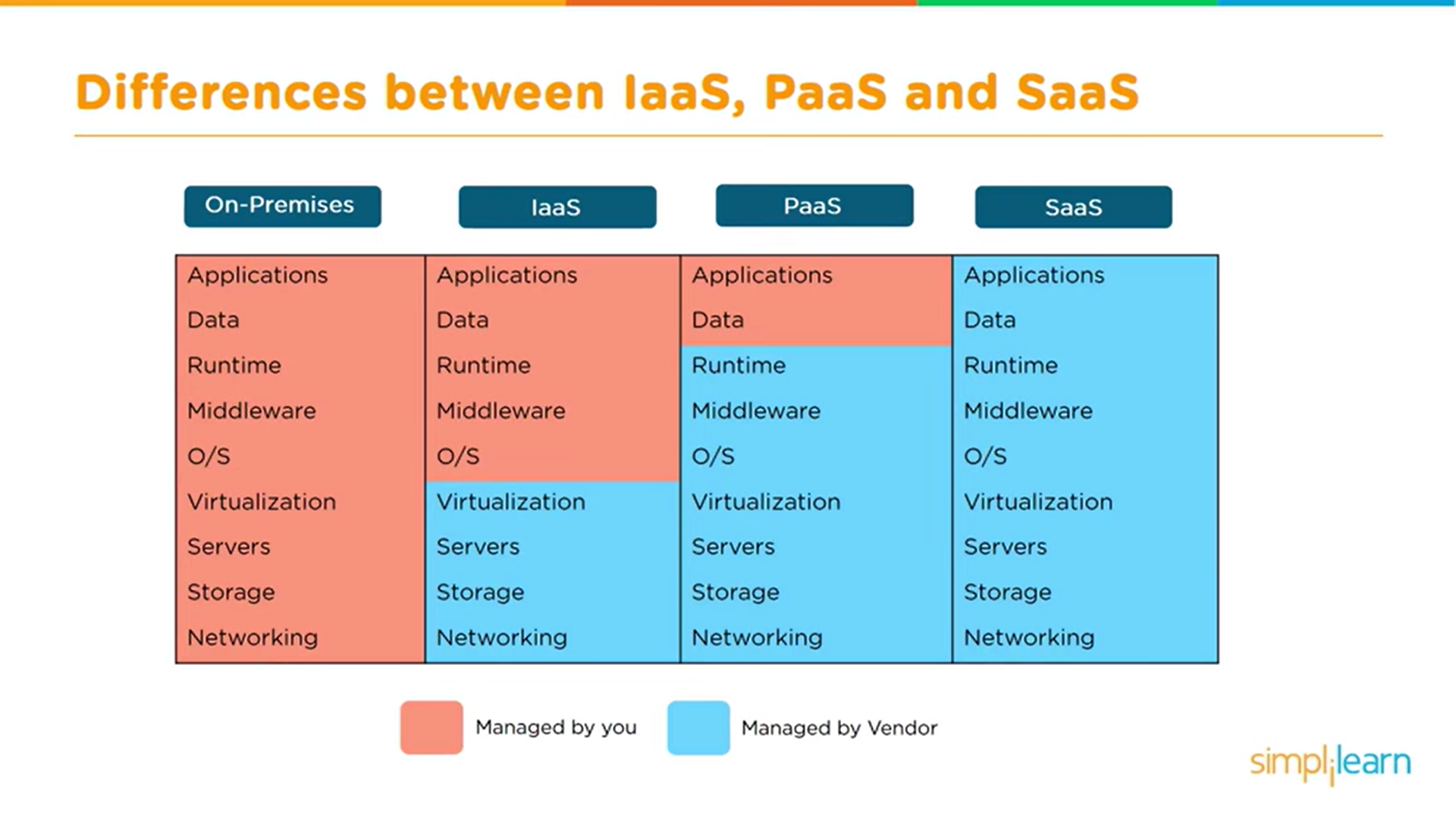
Types of Cloud Services
IaaS:
- provides basic computing infrastructure.
- services are available on pay-for-what-you-use model.
- Ex: AWS Ec2, Google compute engine.
PaaS:
- provide cloud platforms and runtime environment for development, testing and managing apps.
- allows developers to deploy apps without requiring all the related infrastructure.
- Ex: AWS EBS, GCP app engine.
SaaS:
- cloud providers host and manage the software application on a pay-as-you-go pricing model.
- All the necessary software and hardware is provided and managed by the provider, so you don't have to maintain anything.
- Ex: Microsoft Office services, Google Apps.
Task 8 - Introduction to Cybersecurity
Confidentiality, Integrity, Availability (CIA)
The CIA triad stands as a fundamental framework for understanding and implementing effective security measures. These principles form the core principles of security strategies, guiding organizations in safeguarding their digital assets against a myriad of threats and vulnerabilities.
Confidentiality refers to the protection of sensitive information from unauthorized access or disclosure.
Integrity ensures the accuracy, consistency, and reliability of data throughout its lifecycle. It involves safeguarding data from unauthorized alteration, corruption, or tampering.
Availability guarantees that information and resources are accessible and usable when needed by authorized users. It protects against disruptions, downtime, and denial-of-service attacks that could impair system functionality.
Common Types of Cyber Threats
- Malware (Ransomware, spyware, trojan etc)
- Denial-of-Service (DOS) Attacks
- Pishing
- Identity Spoofing (Domain spoofing, Email spoofing)
- Code Injection Attacks (SQL injection, Cross site scripting)
- DNS Tunneling
Cybersecurity Frameworks and Standards
Cybersecurity frameworks and standards provide structured approaches, best practices, and guidelines for assessing, implementing, and managing cybersecurity controls. They help organizations establish effective cybersecurity programs, mitigate risks, and enhance resilience against cyber threats.
Some prominent cybersecurity frameworks and standards:
- NIST Cybersecurity Framework (CSF)
- ISO/IEC 27001
- NIST Risk Management Framework (RMF)
- CIS Controls
- PCI DSS
Hands on experience >>>>>
To Convert & document the following text into Caesar cipher, Pigpen cipher, Morse code, Rail fence cipher, Polybius cipher & Playfair cipher:
Original Text: "Cybersecurity in Marvel".
Caesar Cipher: Each letter in the original text is shifted by 3 positions in the alphabet. For example, 'C' becomes 'F', 'y' becomes 'b', and so on.
Fbehvxfduublq lq Pdunyo
Pigpen Cipher: Each letter is replaced by its corresponding symbol in the pigpen cipher.
🞴🞵🞹🞥🞹🞼🞲🞩🞹🞼🞩🞱 🞻🞹 🞵🞸🞹🞥🞹🞼🞲🞩
Morse Code: Each letter in the original text is represented by a series of dots and dashes.
-.-. -.-- -... . .-. ... -.-- -.. .. -... .-.. --.- ..- .-. -.-- .. -. --. .- .-..
Rail Fence Cipher: The text is written in a zigzag pattern across a specified number of "rails" or lines, then read off in rows.
Cycrry ra ivrleMsebno
Polybius Cipher: Each letter in the original text is represented by a pair of numbers corresponding to its position in a 5x5 grid.
33 25 12 52 34 33 43 23 32 52 33 32 52 35 25 23
Playfair Cipher: Each pair of letters is encrypted using a keyword-driven method based on a 5x5 grid (omitting duplicates and using a keyword to determine grid placement).
KBWVCXDXDKGNAF