Yashaswini's Level - 1 Report
29 / 3 / 2025
CL-CY Level - 1 Report :
Task 1 : OSI
This task helped me understand the interconnectedness between all the electronic devices. OSI stands for Open System Interconnection. This gives a clear idea of the layers involved in the smooth functioning of the internet and software. There are 7 layers involved. These layers with certain protocols ensures that the applications run smoothly. They are :
1. Application Layer :
The application layer, the top layer of the OSI model, is where network applications and user interfaces reside, providing services like email, web browsing, and file transfer by utilising protocols like HTTP, SMTP, and FTP.
Abbreviations of some protocols:
- HTTP : Hyper Text Transfer Protocol
- SMTP : Simple Mail Transfer Protocol
- FTP : File Transfer Protocol
- DNS : Domain Name System
- LDAP : Lightweight Directory Access Protocol
- SSH : Secure Shell
- SNMP : Simple Network Management Protocol
- DHCP : Dynamic Host Configuration Protocol
- TFTP : Trivial File Transfer Protocol
2. Presentation Layer :
The Presentation Layer is the sixth layer of the OSI model, responsible for ensuring data from the application layer is readable by the receiving system by handling data formatting, encryption and compression.
- Data Formatting : It handles the formatting of data, ensuring it's in a readable and understandable format for the receiving application.
- Encryption and Decryption : The presentation layer is responsible for encrypting data before transmission and decrypting it upon receipt, ensuring data confidentiality.
- Data Compression : It can also compress data to reduce bandwidth usage and improve transmission speed
3. Session Layer :
The Session Layer is the fifth layer of the OSI model, which manages and controls connections between applications, establishing, maintaining, and terminating sessions for communication. It ensures data exchange occurs efficiently and in an organized manner, including features like authentication and session checkpointing.
- Session Establishment : It sets up the connection between applications, negotiating parameters like authentication and communication direction (full-duplex or half-duplex).
- Session Management : It oversees the ongoing communication, ensuring data exchange is organized and efficient.
- Session Termination : It gracefully closes the connection when the applications are finished communicating.
4. Transport Layer :
The Transport Layer is the fourth layer in the OSI model, which ensures reliable and efficient data delivery between applications on different computers, using protocols like TCP and UDP, and handles tasks like flow control, error detection, and data segmentation/reassembly.
Key functions of Transport Layer :
- Segmentation and Reassembly : Divides data into smaller packets (segments) for transmission and reassembles them at the destination.
- Error Control : Detects and corrects errors in data transmission, ensuring data integrity.
- Flow Control : Regulates the rate of data transmission to prevent the receiver from being overwhelmed.
Below are a few Transport Layer Protocols that are used in this stage.
- TCP (Transmission Control Protocol) : Provides reliable, connection-oriented communication with features like error checking, flow control, and guaranteed delivery.
- UDP (User Datagram Protocol) : Provides faster, connectionless communication, suitable for applications where speed is more important than reliability, like video streaming.
5. Network Layer :
The Network Layer is the third layer in the OSI model, which facilitates the data transfer between different networks by breaking down segments into packets, assigning logical addresses (like IP addresses), and determining the optimal path (routing) for data transmission.
Key functions of the Network Layer :
- Packetization : It receives data segments from the transport layer (layer 4) and divides them into smaller units called packets.
- Addressing : It uses logical addresses, such as IP addresses, to identify the source and destination networks and devices.
- Routing : The network layer determines the best path (routing) for packets to travel across the network, using routers and routing protocols.
Below are the few protocols used in this stage.
- Internet Control Message Protocol (ICMP) : Used for error reporting and diagnostics, providing feedback on network issues.
- Internet Protocol (IP) : The fundamental protocol for addressing and routing data packets across networks.
- Internet Group Management Protocol (IGMP) : Used by hosts to join and leave multicast groups, and by routers to learn which hosts are members of which multicast groups.
6. Data Link Layer :
The Data Link Layer is the second layer in the OSI model, which handles reliable data transfer across a physical link, framing data into packets, managing physical addressing, and ensuring error detection and flow control.
Key responsibilities of the Data Link Layer :
- Framing : Packages raw data bits into frames, adding headers and trailers for identification and error checking.
- Physical Addressing : Uses MAC (Media Access Control) addresses to identify devices on the network.
- Error Detection and Correction : Implements mechanisms to detect and potentially correct errors that occur during transmission.
- Flow Control : Manages the flow of data to prevent network congestion.
- Media Access Control : Regulates access to the physical transmission medium to prevent collisions and ensure fair access.
7. Physical Layer :
The Physical Layer is the first layer in the OSI model, which deals with the physical transmission of data, including the hardware, cables, and connectors, ensuring raw data bits are transmitted across a physical medium.
Here is a flowchart of the OSI model :
Task 2 : IaaS, PaaS and SaaS
Cloud Computing with AI, or "Cloud AI", combines the power of cloud infrastructure with artificial intelligence, enabling organisations to leverage AI technologies like machine learning and natural language processing without significant upfront investments in hardware or software.
Cloud Computing has three main Cloud Service models : IaaS (Infrastructure as a Service), PaaS (Platform as a Service), SaaS (Software as a Service).
1. IaaS (Infrastructure as a Service) :
- Provides access to fundamental computing resources like virtual machines, storage, and networking, allowing users to build and manage their own applications and infrastructure.
- Users manage the operating systems, applications, and data, while the provider manages the underlying infrastructure.
- Suitable for organizations that need flexibility and control over their infrastructure.
2. PaaS(Platform as a Service) :
- Offers a platform for developers to build, deploy, and manage applications without worrying about the underlying infrastructure.
- Provides tools, libraries, and services for application development and deployment.
- Suitable for development teams that want to optimize their time and resource.
3. SaaS(Software as a Service) :
- Delivers software applications over the internet, allowing users to access and use them without installing or managing them on their own devices.
- Users access the software through a web browser or application, and the provider manages the software and infrastructure.
- Suitable for users who need easy access to software applications without managing them.
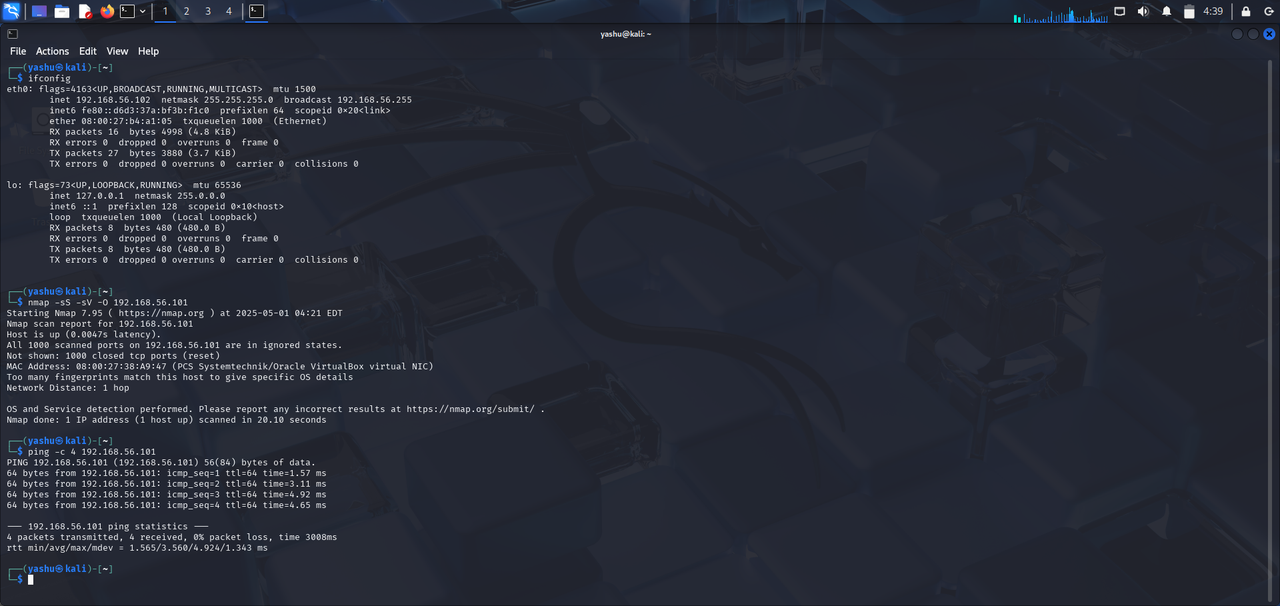
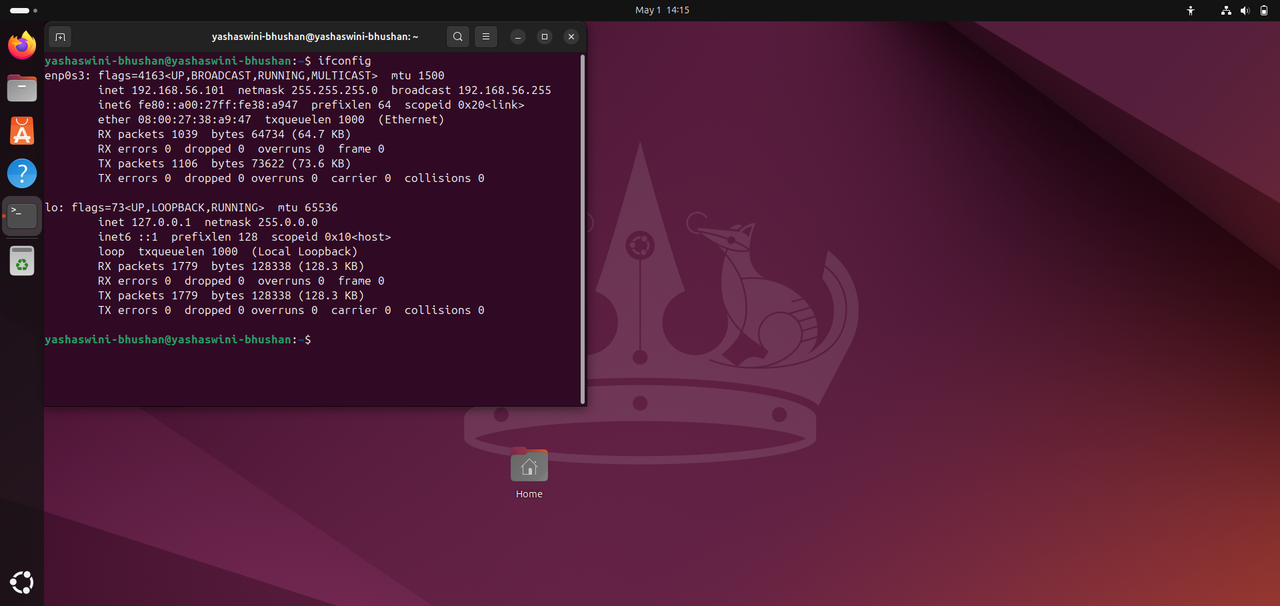
Task 3 : Kali Linux
This task helped me understand the ways an Operating System could be set up in another Operating System using Virtual Machine. I set up Kali Linux, a powerful Linux distribution used for penetration testing and security auditing, on my Windows. I understood the concepts of IP's required for penetration test and how they require both the OS to remain on the same network.
Kali Linux is a Linux distribution designed for cybersecurity professionals, used mainly for penetration testing and ethical hacking.
Virtual Machine is a software that emulates a physical computer, allowing multiple operating systems to run on one physical device.
Nmap is the powerful network scanning tool used for discovering devices and services on a network. It provides information about open ports, services running on those ports, operating systems, and other details.
Penetration Test is a simulated cyber attack used to identify and exploit security weaknesses in systems, networks, or applications.
Task 4 : Socket.IO
A Socket is an endpoint for sending or receiving data across a computer network. Socket.IO allows bi-directional communication between client and server.
Common uses of Socket.io are:
- Chat applications
- Live notifications
- Real-time analytics
- Multiplayer games
- Collaborative tools
While working on this task, I learnt about the server, how it connects users and tracks their actions. I made the website using HTML, Express.js, and Socket.io and gave it a proper appearance using CSS.
A glimpse of the website's appearance:
Task 5 : Encryption Techniques - Secure Messaging App
Data Encryption is one of the many ways organisations can protect their data. Encryption turns plaintext into ciphertext, which requires the use of a unique cryptographic key for interpretation.
Types of Encryption :
1.Symmetric encryption: A single secret key is used to encrypt plaintext and decrypt ciphertext. Both the sender and receiver have private access to the key, which can only be used by authorised recipients. It is also known as Private Key Cryptography.
2.Asymmetric encryption : This method is also known as Public Key Cryptography. Two keys are used: a public key and a private key.
- Public Key: Either publicly available or shared with authorised recipients.
- Private Key: It is required to access data encrypted by the public key.
Asymmetric encryption offers another level of security to the data, which makes online transfers safer.
I made an encrypted server using Python and cryptography, having symmetric keys. I learnt how the symmetric keys play a major role in encrypting and decrypting the messages.
Below is the screenshot of the server:
Below is the screenshot of the client:
Task 6 : Web-Scraping
Web-Scraping is a technique of collecting data from websites. It involves using programs or scripts to send requests to a website, retrieve the HTML content, and extract specific information like text, images or links.
BeautifulSoup is a Python library used for parsing HTML and XML documents to extract data easily from web pages.
TCP(Transmission Control Protocol) is a core network protocol that ensures reliable, ordered, and error-checked delivery of data between devices over the Internet or other networks.
I learnt about IP addressing and the bot protection that the websites had, for which the requests were sent using user agents, which tell the website what kind of device or software is accessing it.
BeautifulSoup can only parse HTML websites. It can't render or interact with JavaScript.
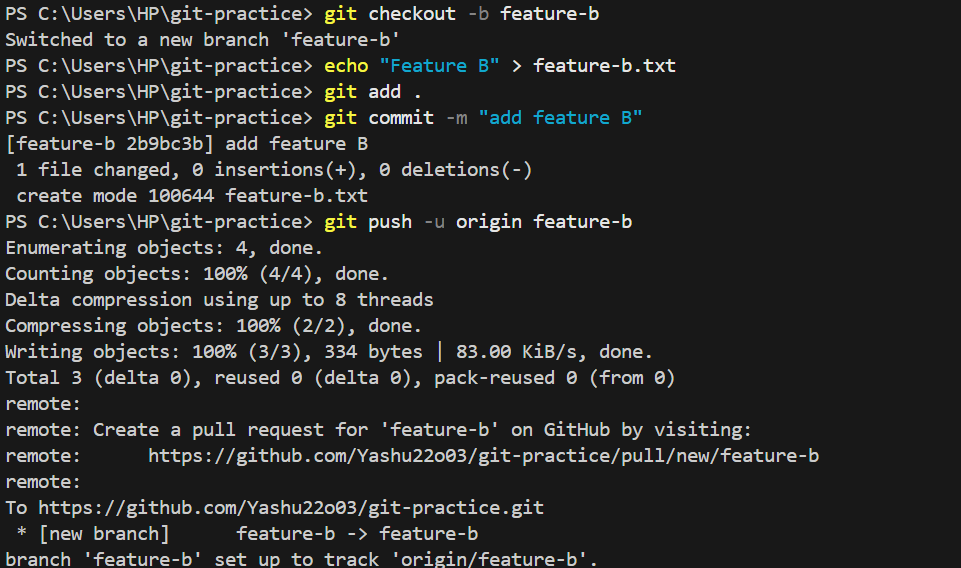
Task 7 : Working of Version Control
Version control is a system that records changes to files over time, so one can track revisions, collaborate with others, and revert to previous versions if needed.
Basic Git Commands :
- git branch : The
git branchcommand is used to list, create, or delete branches.
- Create a new branch :
git branch branch-name- List all branches :
git branch- Create a new branch and switch to it :
git checkout -b branch-name- Switch branches :
git checkout branch-name
- git merge : It is used to merge the history and changes of one branch into the current branch.
Basic Syntax :
git merge branch-name
- git revert : It is used to undo a commit by creating a new commit that reverses the changes made by a previous one without rewriting the history.
** Basic syntax :**
git revert commit-hash
- git cherry-pick : It applies the changes from a specific commit (or commits) onto your current branch, regardless of where they came from.
** Basic syntax :** git cherry-pick commit-hash