
BLOG · 14/9/2023
CL-CY Level 1 (overflowed...)
Flooded part of the report

This Article is yet to be approved by a Coordinator.

BLOG · 14/9/2023
Flooded part of the report

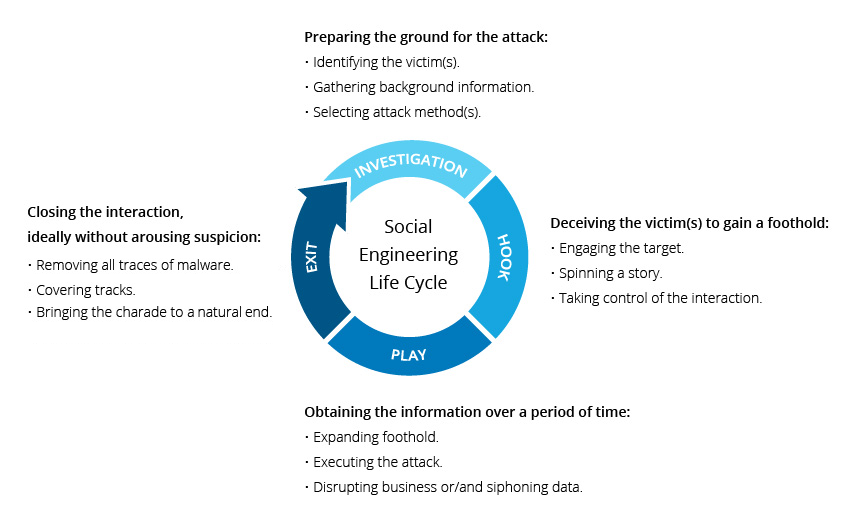 \nTechniques of Social Engineering: Baiting, Scareware, Pretexting\n \n\n\n\n\n### Ciphers:\n\n1. Ceaser Cipher: It is one of the simplest and most widely known encryption techniques. It is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet.\n\nPlain Text: Cybersecurity in Marvel\n\n
\nTechniques of Social Engineering: Baiting, Scareware, Pretexting\n \n\n\n\n\n### Ciphers:\n\n1. Ceaser Cipher: It is one of the simplest and most widely known encryption techniques. It is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet.\n\nPlain Text: Cybersecurity in Marvel\n\n\nShift 10: \n🠜10 (🠞16)\t`Milobcomebsdi sx Wkbfov`\n🠞10 (🠜16)\t`Soruhiuskhyjo yd Cqhlub` \n\n\n2. Pigpen Cipher: is a geometric simple substitution cipher, which exchanges letters for symbols which are fragments of a grid.\n\n \n\nEncoded:
\n\nEncoded:  \n\n3. Morse Code: Morse code is a method used in telecommunication to encode text characters as standardized sequences of two different signal durations, called dots and dashes, or dits and dahs.[3][4] Morse code is named after Samuel Morse, one of the inventors of the telegraph.\n\n
\n\n3. Morse Code: Morse code is a method used in telecommunication to encode text characters as standardized sequences of two different signal durations, called dots and dashes, or dits and dahs.[3][4] Morse code is named after Samuel Morse, one of the inventors of the telegraph.\n\n \n\nEncoded:
\n\nEncoded: -.-. -.-- -... . .-. ... . -.-. ..- .-. .. - -.-- / .. -. / -- .- .-. ...- . .-..\n\n4. Rail Fence Cipher: The rail fence cipher (also called a zigzag cipher) is a classical type of transposition cipher. It derives its name from the manner in which encryption is performed, in analogy to a fence built with horizontal rails.\n\n\nGrid[rails-3]:\n \nC r u y v \n y e s c r t n M r e \n b e i i a l\n \n\nencoded text: Cruy v yescrt nMre beiial \n\n\n5. Polybius CIpher: It is used for fractionating plaintext characters so that they can be represented by a smaller set of symbols, which is useful for telegraphy, steganography, and cryptography. \n\nGRID: \n\n| \ | 1 | 2 | 3 | 4 | 5 | \n|:-:|:-:|:-:|:-:|:-:|:-:|\n|1 | A | B | C | D | E |\n|2 | F | G | H | I | J |\n|3 | K | L | M | N | O |\n|4 | P | Q | R | S | T |\n|5 | U | V | W | X | Y |\n\n\n\n\nencoded: 135512154344151351432445552434331143521532\n\n6. Playfair Cipher: The Playfair cipher uses a 5×5 grid of letters, and encrypts a message by breaking the text into pairs of letters and swapping them according to their positions in a rectangle within that grid.\n\nRules: \n7. If both letters are the same (or only one letter is left), add an \X" after the first letter. Encrypt the new pair and continue. Some variants of Playfair use "Q" instead of "X", but any letter, itself uncommon as a repeated pair, will do.\n\n8. If the letters appear on the same row of your table, replace them with the letters to t\n9. Heir immediate right respectively (wrapping around to the left side of the row if a letter in the original pair was on the right side of the row).\n\n10. If the letters appear on the same column of your table, replace them with the letters immediately below respectively (wrapping around to the top side of the column if a letter in the original pair was on the bottom side of the column).\n\n11. If the letters are not on the same row or column, replace them with the letters on the same row respectively but at the other pair of corners of the rectangle defined by the original pair. The order is important – the first letter of the encrypted pair is the one that lies on the same row as the first letter of the plaintext pair.\n\ngrid: Playfair square\n| M | A | R\t| V\t| E |\n| -- | -- | -- | -- | -- |\n| L | B\t| C\t| D\t| F |\n| G | H\t| I\t| K\t| N |\n| O | P\t| Q\t| S |\tT |\n| U | W | X\t| Y |\tZ |\n\n\nencrypted: DXFAVQRFXMNQXKGERVEMCU"